Recorded Future with VMware Carbon Black Cloud
Overview
Recorded Future and VMware Carbon Black have created a series of integrations to leverage the strength of each other’s products in the product consoles. The first integration pushes Risk List IOCs to Carbon Black Cloud (CBC) Enterprise EDR to watch for any activity on any of the IOCs in the list on the endpoints. The second integration pulls endpoint Alerts from CBC Enterprise EDR into the Recorded Future Intelligence Card to show any alerted activity on an IOC while researching an indicator.
For more information on ingesting Threat Intelligence into CBC Enterprise EDR, see Create Custom Feeds and Ingest Third-Party Feeds into Enterprise EDR from Raj Sahota.
Pre-Requisites
- Current Customer of CBC Enterprise
- The following assumes that Carbon Black sensors have been deployed and properly configured.
- License to Recorded Future
Carbon Black Cloud Data in Recorded Future
By ingesting Alerts from CBC Enterprise EDR customers are able to gain context from Recorded Future’s console as they are investigating an IOC without leaving the console. This allows the analyst to operate more efficiently without having to jump between multiple product consoles while investigating threats.
Configuration
To configure the integration you will need to start be getting some API credentials from the CBC console.
Log into the CBC console and navigate to Settings > API Access. From here, click on the Access Levels tab at the top and click Add Access Level.
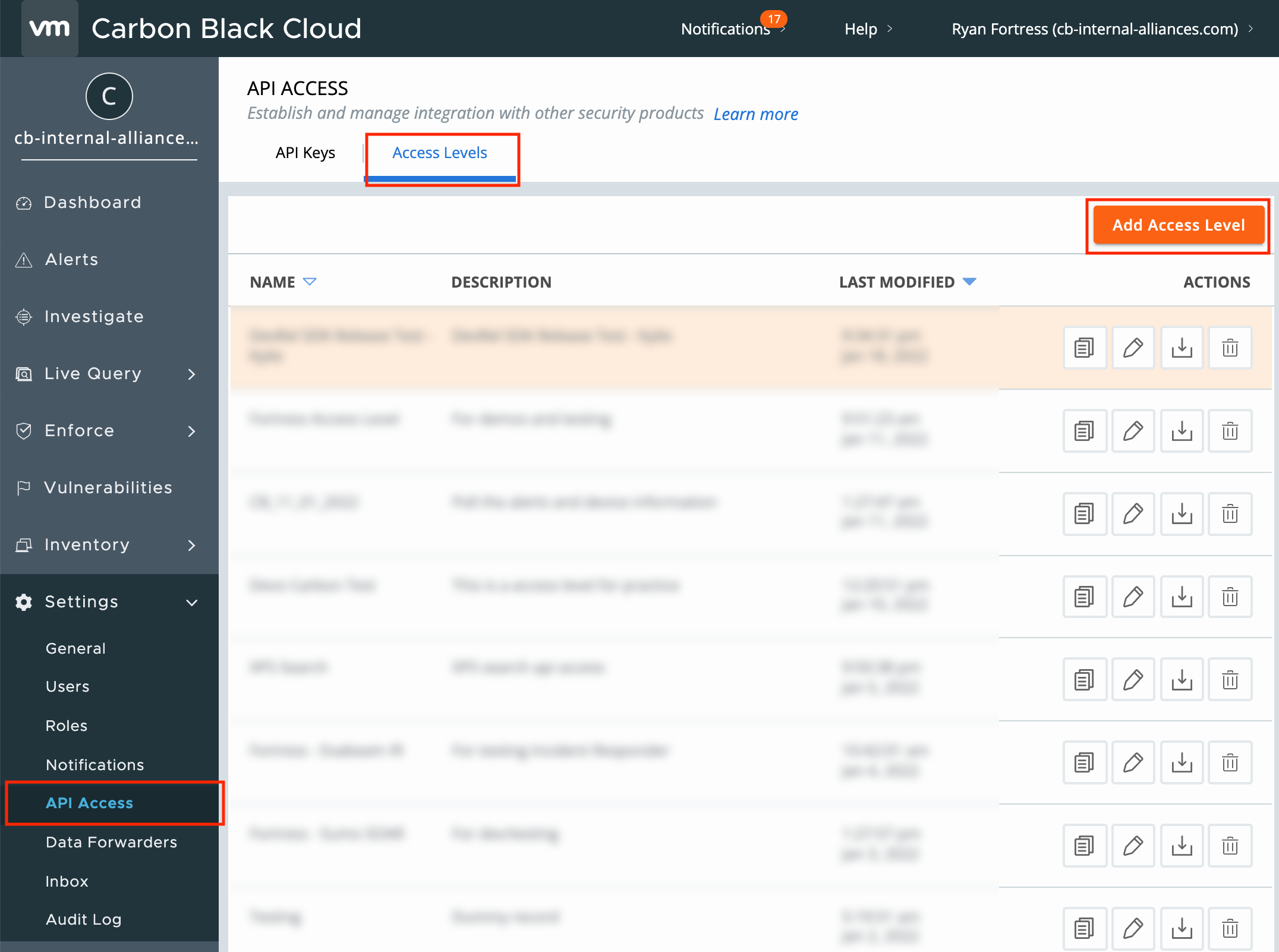
Fill in the name, description and select the Alerts – READ role, then click Save.
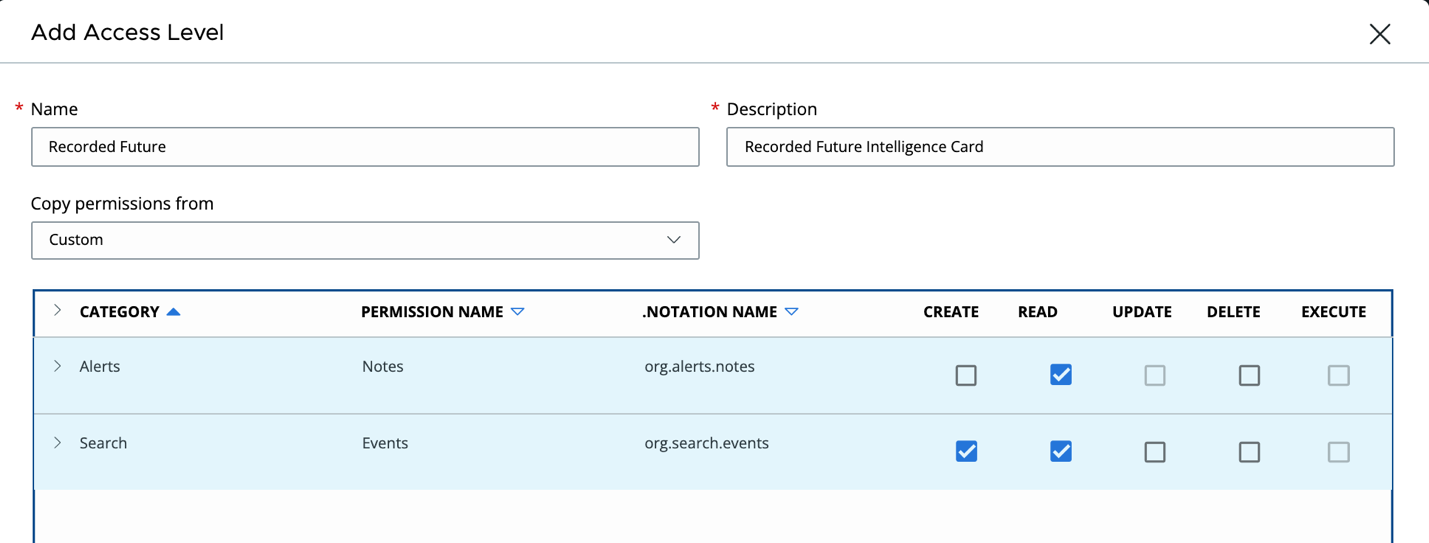
Now we have the Access Level configured, we can create an API key that uses the Access Level. Click on API Keys at the top and click Add API Key. Fill in the name and description for the integration. Next select Custom from the Access Level type, then select the Access Level you create, then click Save.
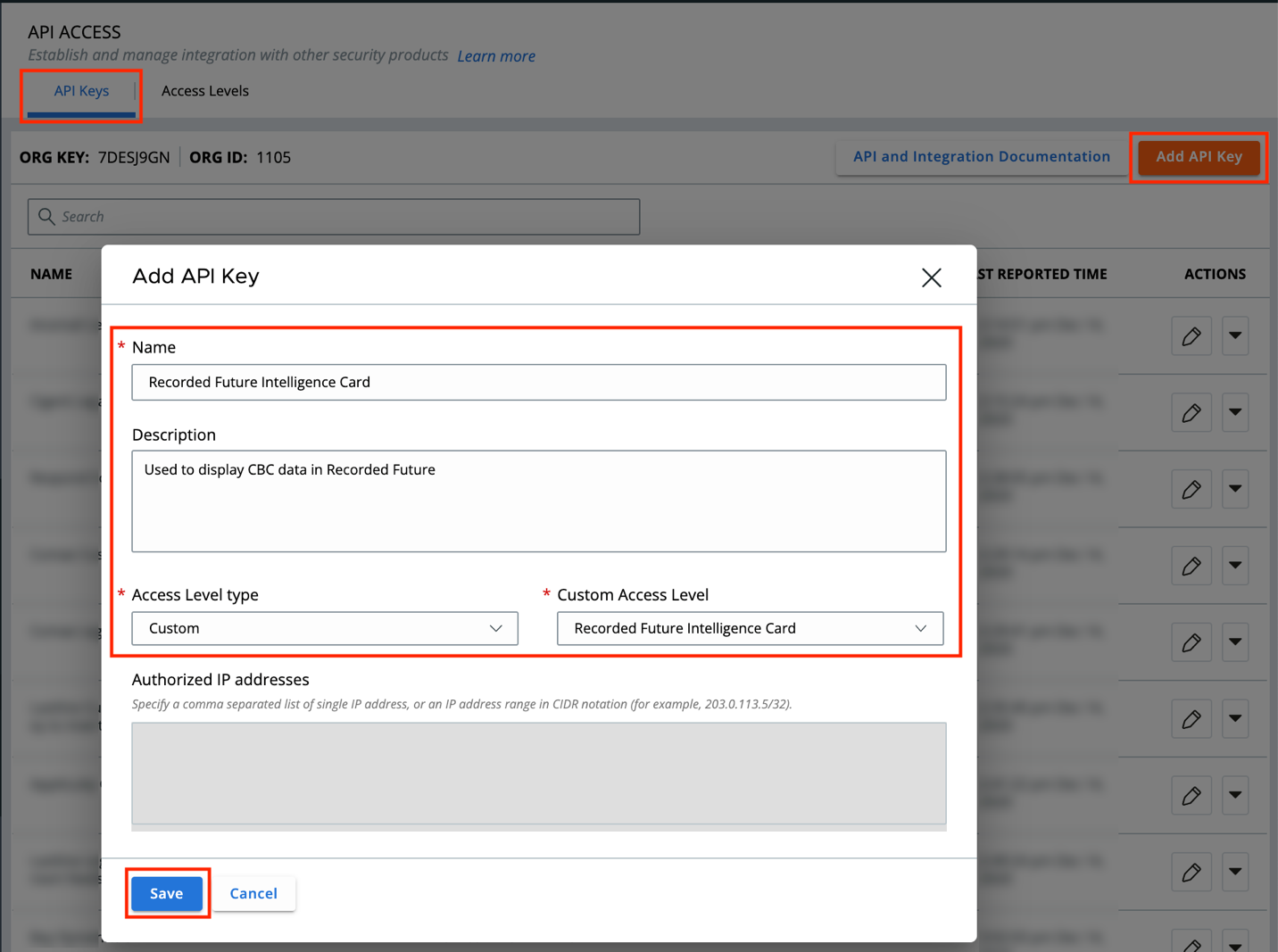
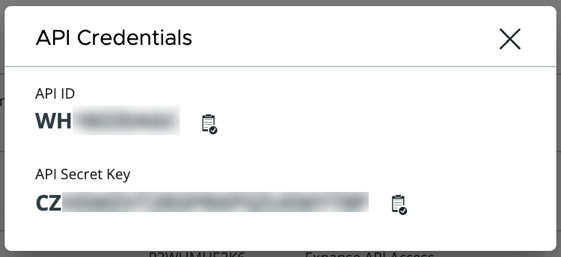
You will be presented with the API credentials that you will need to copy / paste into the Recorded Future console.
Open a new tab and navigate to your Recorded Future console. Once logged in navigate to Menu > Extensions.
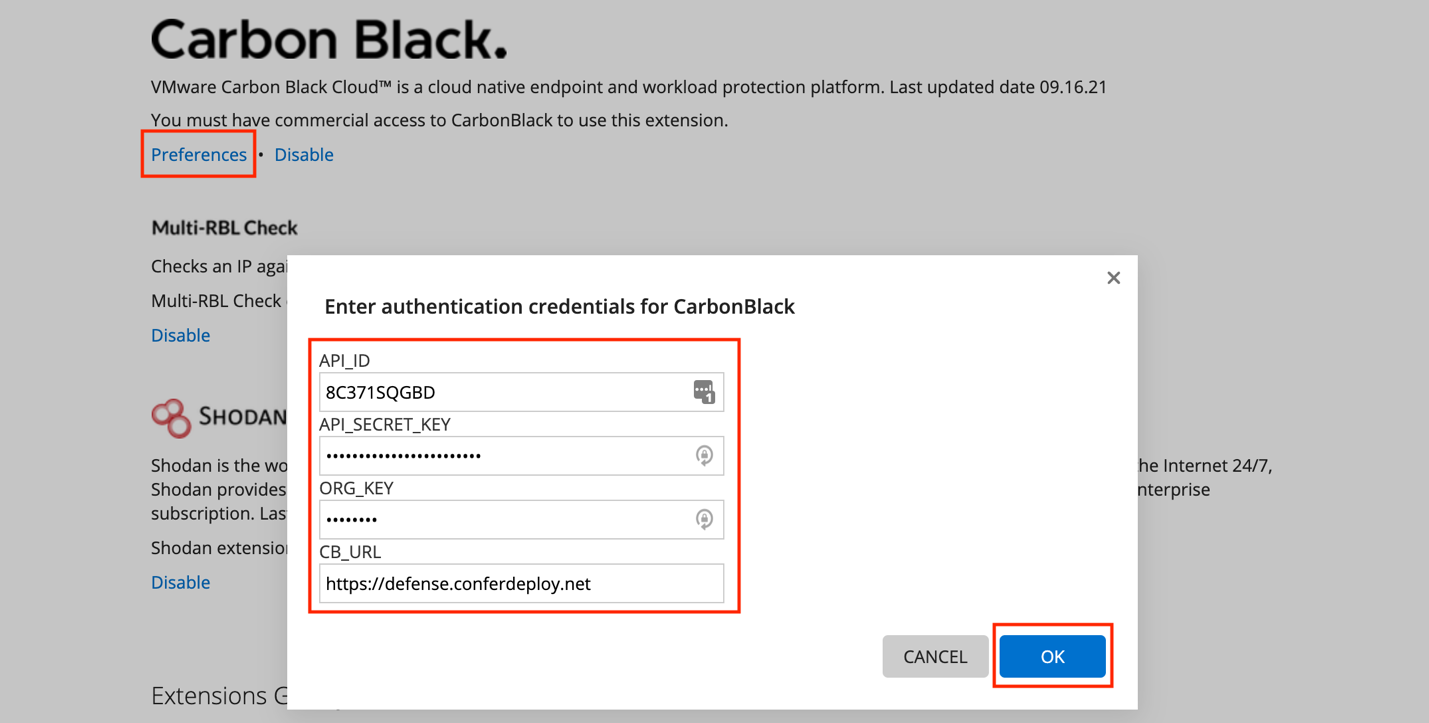
There you will see the Carbon Black section where you can select Preferences. Enter the API ID, API Secret Key, Org Key and URL for your Carbon Black Cloud instance. Once complete, select OK.
Operationalizing
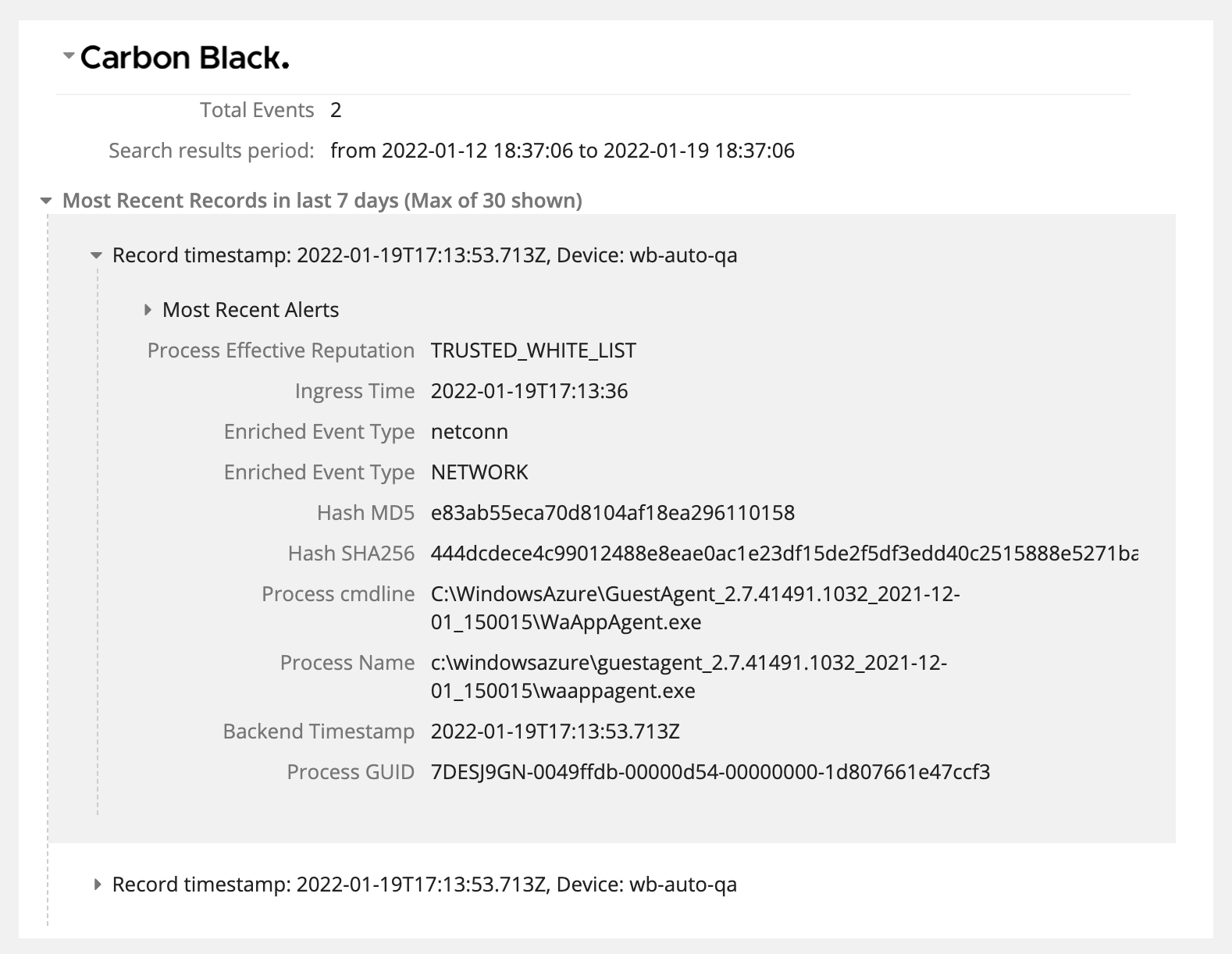
Now when you search for an IOC in the Recorded Future console, you will see the Carbon Black Cloud card. When you expand the card you will see any Alerts on that IOC from Carbon Black Cloud.
Recorded Future Data in Carbon Black Cloud
By sending Recorded Future’s Risk List intel to CBC Enterprise EDR customers are able to monitor for and alert on any endpoint activity on those IOCs. This allows the SOC to respond faster to threats and remediate if needed.
Configuration
This integration is configured by Recorded Future’s support team. To get this integration up and running, the customer will need to open a support ticket with Recorded Future asking for the integration to be enabled.
Once the data is being pushed into CBC Enterprise EDR we can enable the Feed and start correlating the IOCs with endpoint activity. To do this, open the CBC console and navigate to Enforce > Watchlists > Add Watchlists.
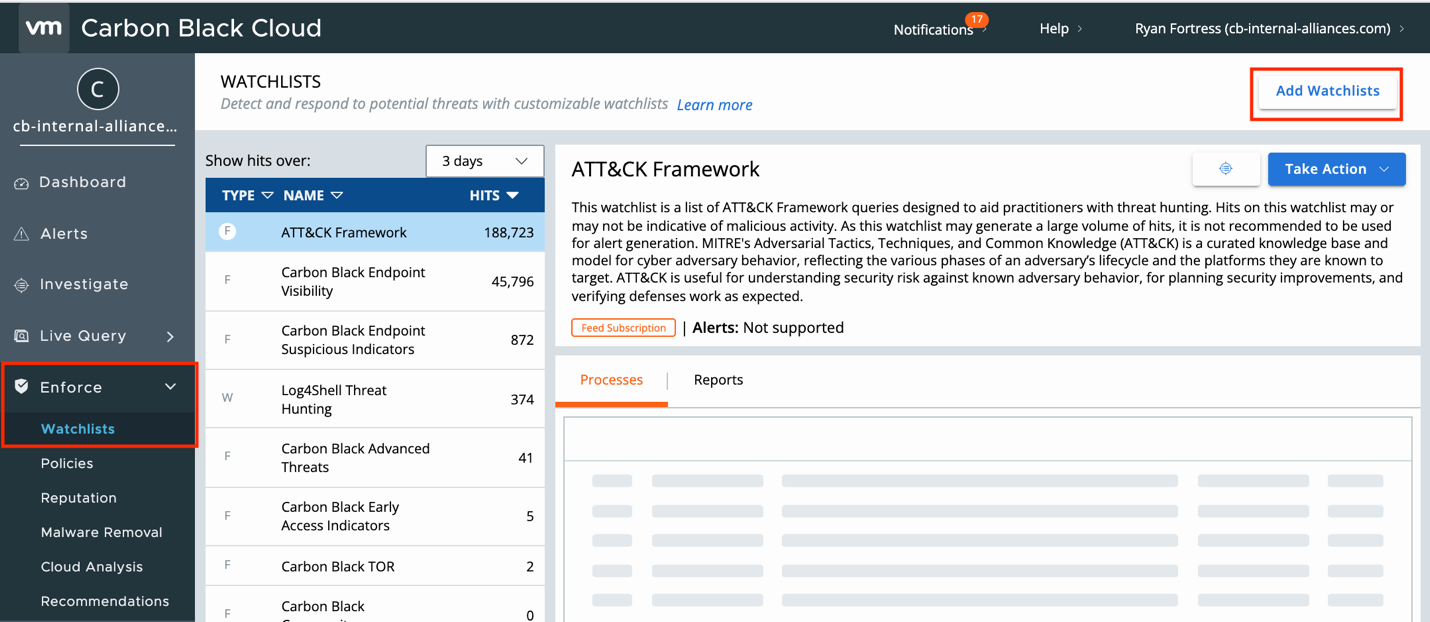
Now we can see the feeds that are available but are not being used for analysis. To add a feed, select the checkbox next to its name and click Subscribe.
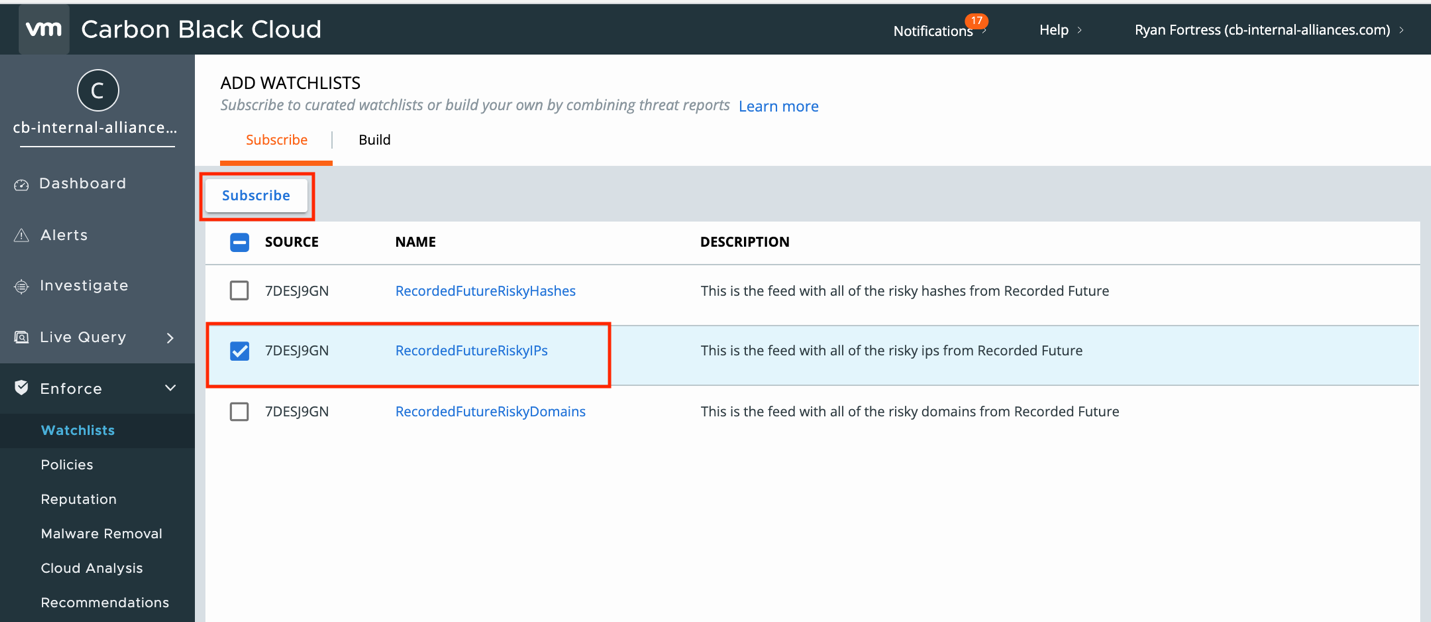
Now the feed has been added to our Watchlists and endpoint activity is being correlated with the IOCs from the feed. Any correlations will create a Hit, but it will not generate an Alert. To enable Alerts, select the feed and select Take Action > Edit and the Edit Watchlist dialog will open.
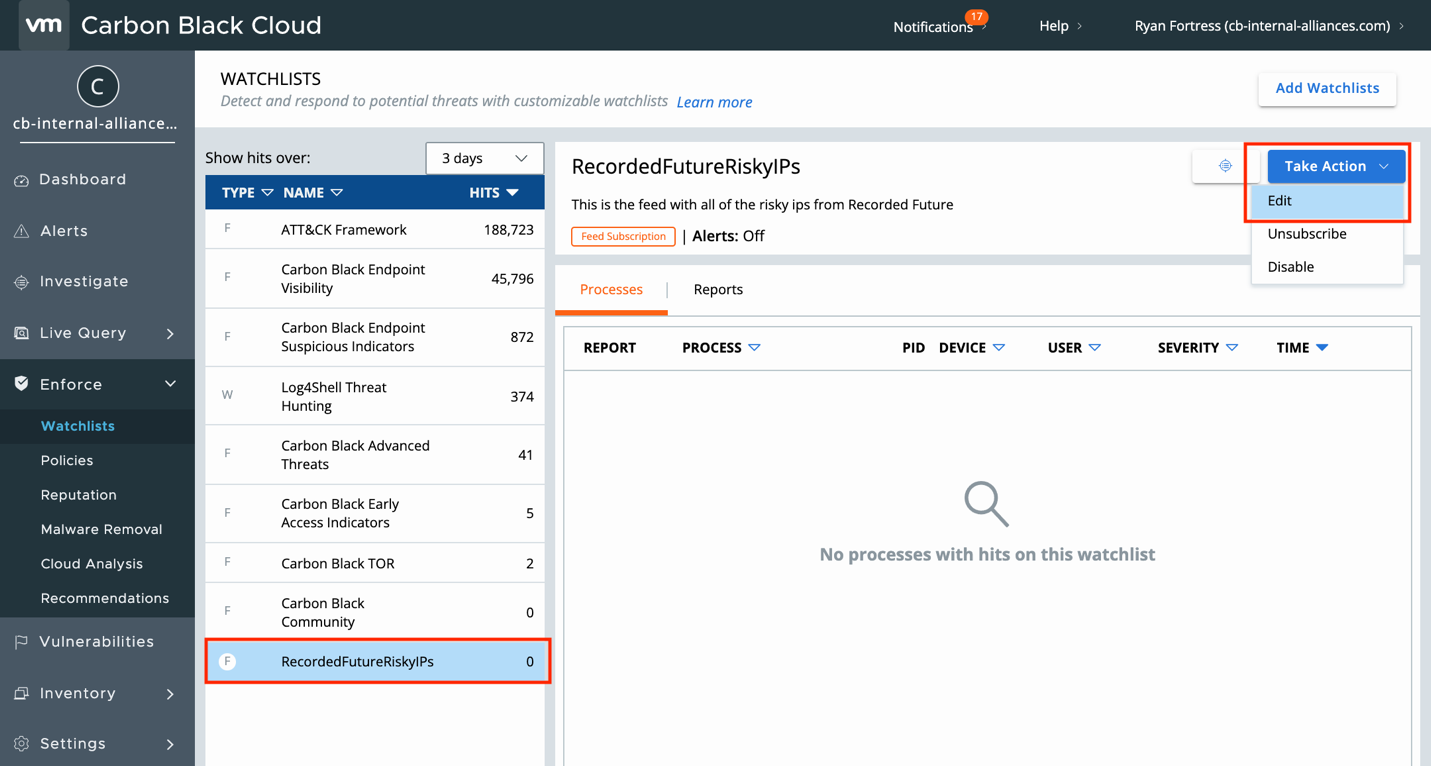
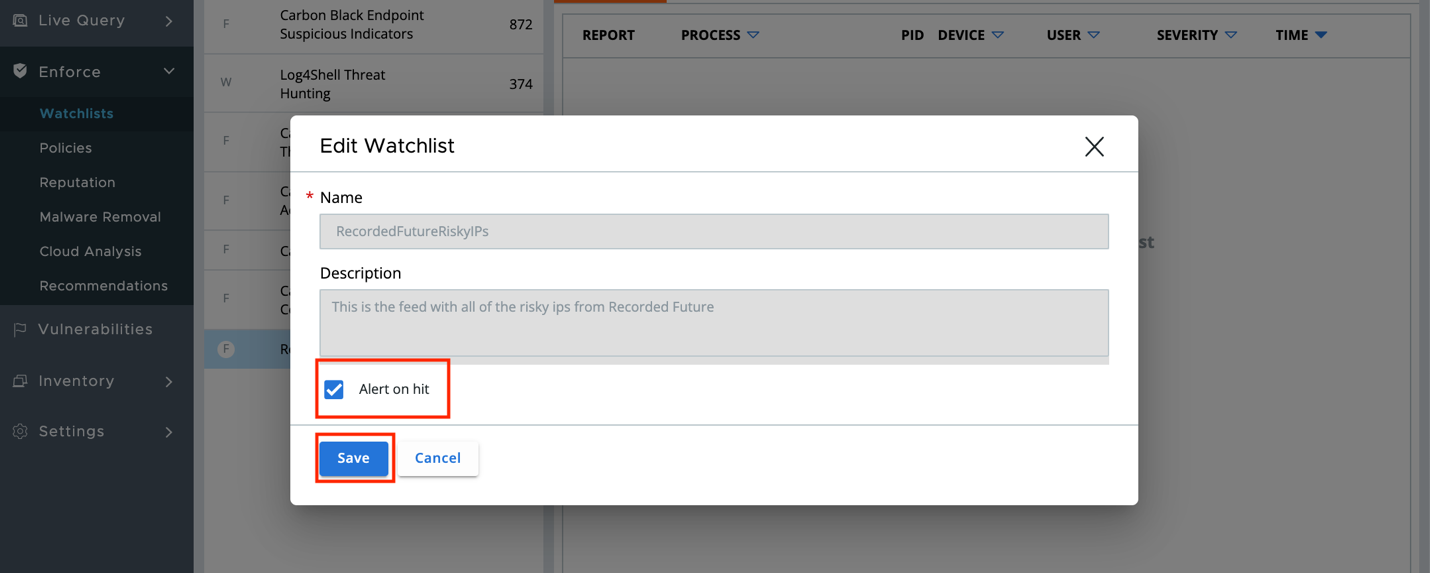
In the dialog, select Alert on hit and click Save.
Operationalizing
Now that the data is being ingested and correlated, we will start to see some Hits and Alerts appear from the activity. There are two ways to view the hits on the IOCs. The first is to look at the Watchlist Hit activity. To do this, select the Watchlist and the Hits will appear.
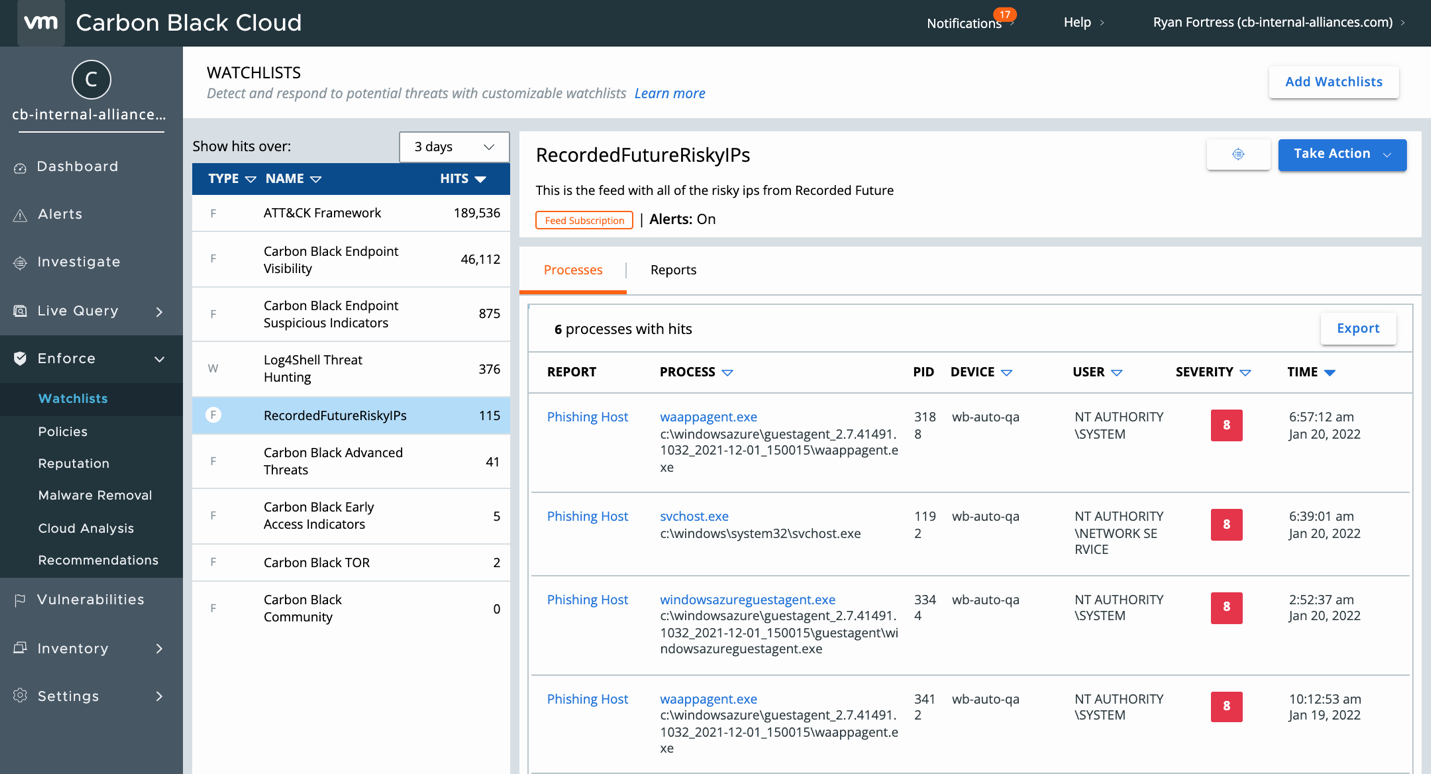
From here we can pivot into the process details by clicking on the process name, or pivot into the Report to see the IOCs in the report.
The second way to view important information from the Watchlist is to search for any Alerts by the Report ID. While in the Report Hits section, click on the Report name. This will open the report and display all the IOCs. At the end of the URL is the Report ID. Copy that ID and navigate to Alerts.
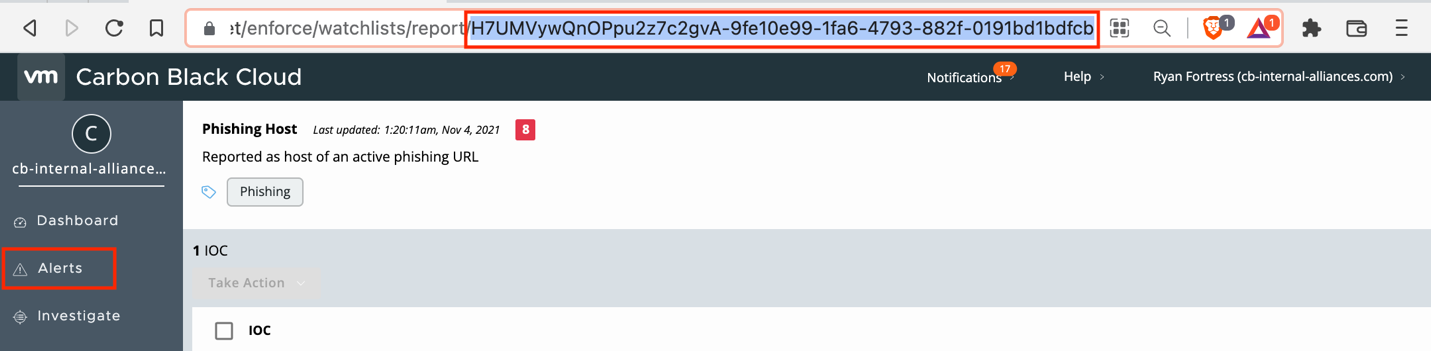
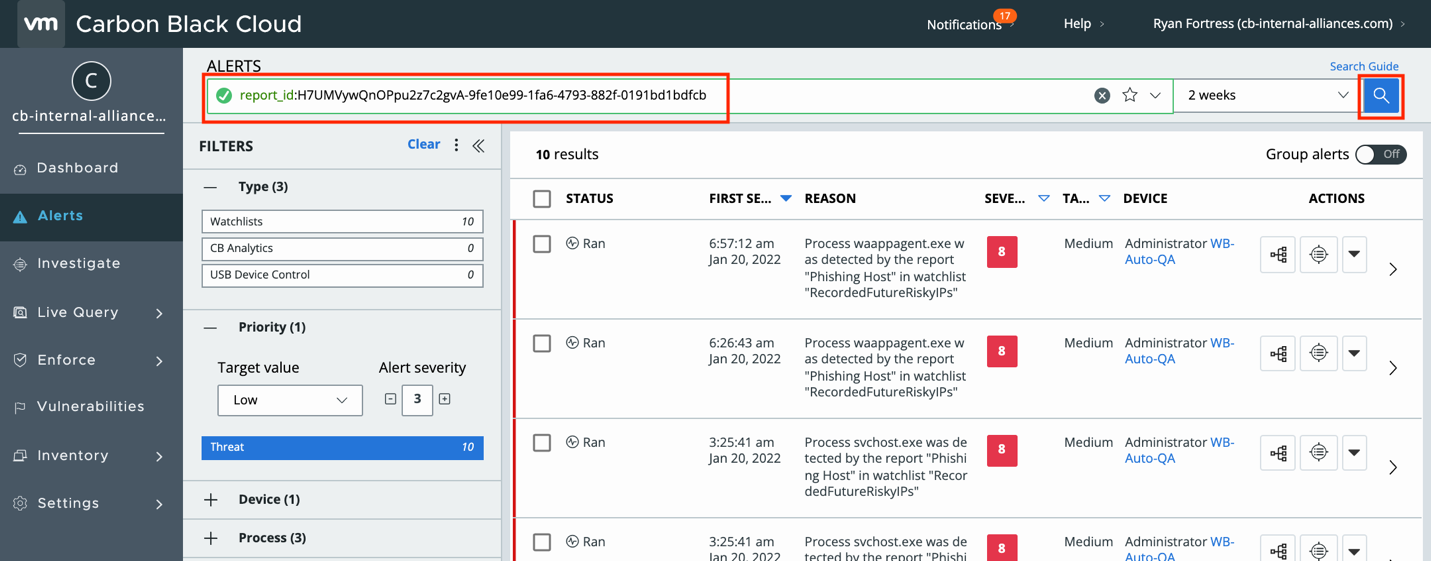
In the Alerts screen, use the report_id field and paste the Report ID to search for any Alerts on that report.
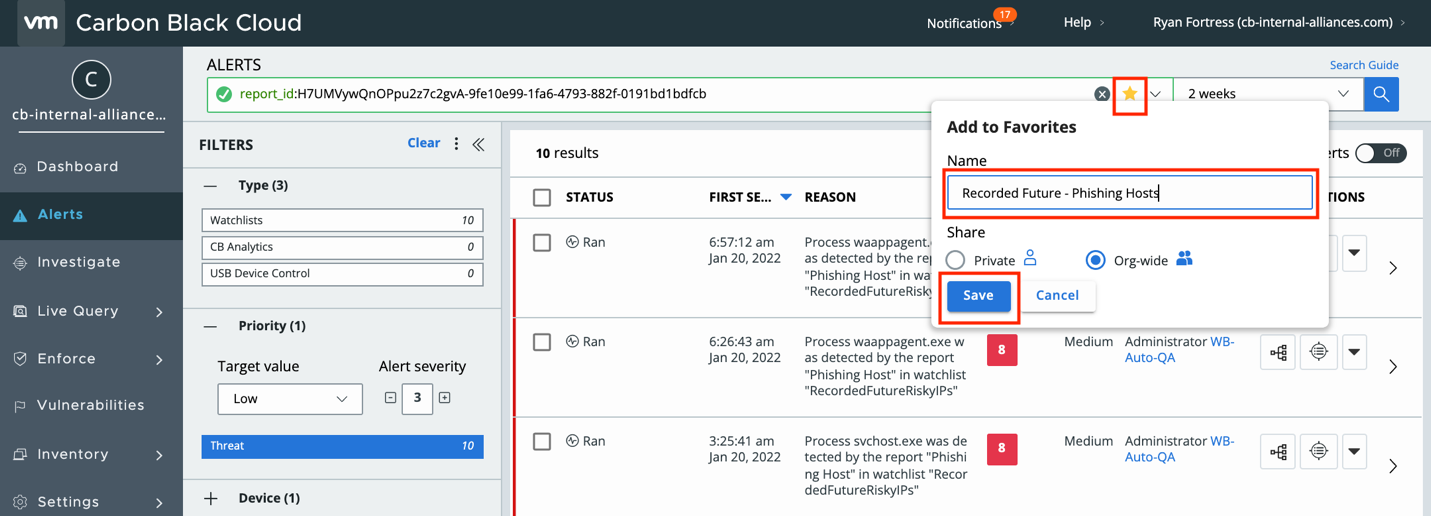
Now we see Alerts from the feed, but we don’t want to paste that Report ID every time. We can save this query using the Favorites feature so we can view these results easily in the future. To do this, click the Star icon, then give it a name and select if this should only be visible to you, or to the whole organization. Finally click Save.
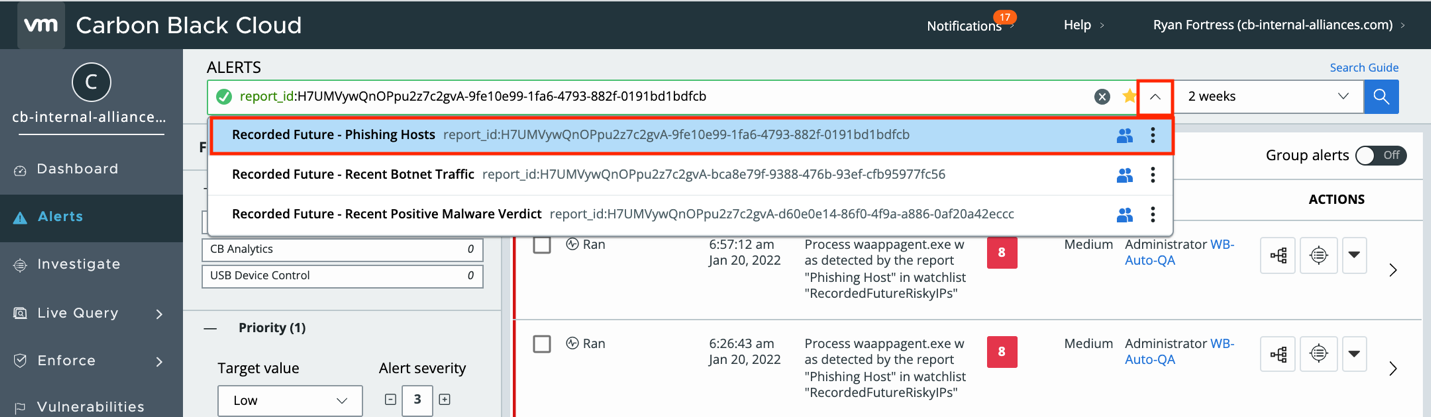
Now any time we want to see the results, we can click the dropdown arrow on the search query and select our favorite.
Summary and Additional Resources
By combining the capabilities of VMware Carbon Black Cloud Enterprise EDR and Recorded Future we are able to make the SOC strong and the investigation/response time shorter for the analyst.
Additional Resources
- Recorded Future’s Integrations Page
- Create Custom Feeds and Ingest Third-Party Feeds into Enterprise EDR
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2022/01/20 |
|
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware Security Business Unit Technical Marketing at SBU_tech_content_feedback@vmware.com .
About the Author
Ryan is the Sr. Tech Alliance Engineer with VMware Carbon Black and has extensive experience in cyber security with a focus on Threat Intelligence. He is an Army vet, spent 6 years in the Middle East, wrote a security operations platform for the Space and Naval Warfare Center, and now helps create and strengthen alliances with the best companies in our industry.
