ZScaler Integration with Carbon Black
Introduction
Zscaler and VMware Carbon Black have joined forces to release a series of integrations. These integrations are between Zscaler's ZIA Sandbox, Zscaler’s ZPA, VMware Carbon Black Cloud (CBC) Endpoint Standard, and CBC Enterprise EDR. This combination gives our customers the ability to leverage their technologies to tell a better story together.
Zscaler ZIA Sanbox and Carbon Black Cloud
While Zscaler can scan all files before they reach the endpoint as they come through the network, what happens when a file comes in via another method, or prior to sensor installation?
There are two methods for this integration. The first is a lookup from the Zscaler ZIA console to see if a hash being investigated has been seen by CBC. The second is the CBC / Zscaler Sandbox Connector which will scan for any processes of endpoints running CBC Enterprise Standard or CBC Enterprise EDR. Any results will kick off a series of actions.
CBC Processes in Zscaler ZIA
Configure Carbon Black Cloud
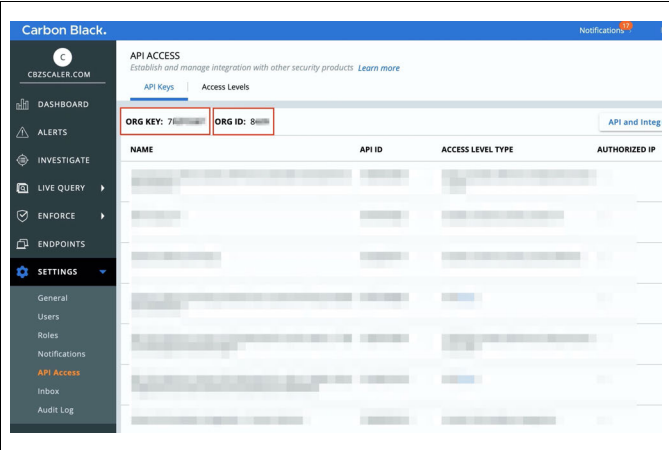
- Create Carbon Black Cloud API Key. In the Carbon Black Cloud console navigate to the API Access section. Settings > API Access.

- Note your Org Key and Org ID. This will be needed later in the Zscaler UI. Navigate to Access Levels. Create a new API Access level with the following permissions:
- Execute only for Device Quarantine
- Create and Read for Threat Hunter events
- Read-only for Device General information

- Once completed, click Save. Navigate back to API Keys and click on create new API Key with the newly created Access Level

- Then click Save. Take note of your API ID and API Secret Key for the ZIA UI Configuration.

Configure Zscaler Internet Access (ZIA)
- Navigate to your Zscaler console. Navigate to: Administration> Partner Integration> Carbon Black.
- Select the appropriate tab per your products licensed. Either CB Defense (Endpoint Standard), Threat Hunter (Enterprise EDR) or Both.
- Paste your Carbon Black Cloud API ID/Secret key and Org ID/key here. Cloud Service Hostname depends on the location of your Carbon Black tenant. Please refer to the link below for identifying the Hostname pertinent to your CB environment (Appendix C). Click Save.

- Clicking Save will trigger an API call to Carbon Black to verify the credentials. If you see the green message “Valid API token(s)”, then you have successfully configured the API connection for the ZIA sandbox and Threat Hunter integration to work.
Activate Pending ZIA Configuration
Anytime you make a change in ZIA, you will see a number over the Activation icon on the left-hand side menu. This lets you know that you have changes pending in the queue for activation. When you are ready to commit all changes in the queue, hover the mouse over the Activation menu and click the blue Activate button.

Operationalizing Zscaler and Carbon Black Cloud
Viewing Carbon Black Cloud Endpoint Hits
Once Malware is detected by Zscaler Cloud Sandbox this will automatically correlate with Carbon Black Endpoint device information. Below steps are shown within the Zscaler admin portal.
- Navigate to Analytics > Insights > Web Insights
- Then click on the Logs tab and Add Filter.

- Enter “Threat Class”.
- Select Sandbox as the Threat Class. Click Apply Filters.
- Once you click Apply Filters, if the file in question was detonated by Zscaler sandbox or is currently being detonated by Zscaler sandbox - you’ll see corresponding log entries on right.

- Click on a MD5 hash to select View Carbon Black Endpoint Hits Report.

By clicking Contain you will trigger an API call to Carbon Black to cut off network access to that endpoint.
The Endpoint Status will then change to Quarantined.
Zscaler ZIA Sandbox Lookups from CBC
Pre-Requisites
- Current Customer of CBC Enterprise EDR and/or CBC Endpoint Standard
- The following assumes that Carbon Black sensors have been deployed and properly configured.
- License to Zscaler ZIA Sandbox
- Python 3.x with sqlite3
Github Repo
The integration is available on Carbon Black’s Github repository. Clone the repository to a local (or cloud) device and configure the integration by following the instructions in the README.md.
Once the integration is configured you can schedule it to run on a cron. We recommend once every 30 minutes. Each time the connector runs it will pull all processes matching the reputations defined in the config.conf file. For each process that is returned, the connector will look in a local database of Zscaler results, or reach out to Zscaler’s Sandbox over API for any reports on the hash. Any hits will cause the connector to run the actions defined. Any combination of actions can be enabled, which are:
Action options consist of:
- Adding to a CBC Enterprise EDR Watchlist Feed
- Passing the process and sandbox report to a webhook
- Running a script (default action is to stop the process and delete the file)
- Isolating the endpoint
- Moving the endpoint into a policy
Most of the actions are straightforward, but two are worth discussing in more detail.
- The webhook is intended to enable integrations into SOAR workflows. It provides an object with the process from CBC, the sandbox report from Zscaler ZIA, and the sha256 in question. (
{ “process”: <process info>, “report”: <zs report info>, “sha256”: <sha256> }). - The script has the intent to serve as an example, but can be customized to enable a user’s specific needs. Out of the box the script will leverage Live Response to establish a session to the device, look for the process and if running stop it, and delete the file from the endpoint. This script can be customized to enable any number of workflows and can run for each positive result.
For a general overview on how this connector works, here is a flow diagram of the process:

Zscaler ZPA Posture Check
ZPA Posture Check
The device posture profile is a set of criteria that a user’s device must meet in order to access applications with ZPA. You can select a device posture profile when configuring access policies in the ZPA Admin Portal. However, you must configure device posture profiles in the Zscaler Client Connector Portal.
Client Connector (Zapp) will check for the presence of running Carbon Black Cloud agent on the endpoint. This will constitute the posture check that can be tied to access policies This posture check is supported for laptops/desktops running MacOS or Windows. If a device does not meet the criteria for the posture check (i.e. the CBC agent isn’t installed/running) then the user is redirected to a page letting them know why the access was blocked.
Summary and Additional Resources
Additional Resources
- Carbon Black Cloud and Zscaler GitHub
- Zscaler Integration Resources
- Zscaler + VMware Carbon Black | Partner Solutions
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2021/12/01 |
|
About the Author and Contributors
Ryan is the Sr. Tech Alliance Engineer with VMware Carbon Black and has extensive experience cyber security with a focus on Threat Intelligence. He is an Army vet, spent 6 years in the Middle East, wrote a security operations platform for the Space and Naval Warfare Center, and now helps create and strengthen alliances with the best companies in our industry.
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware Security Business Unit Technical Marketing at SBU_tech_content_feedback@vmware.com .