Securing Multi-Cloud - Solution Guide
Welcome to the World of Securing Multi-Cloud
In the world we used to know, when Amazon sold books and Microsoft software came in a box stuffed full of floppy disks, enterprise applications typically ran in a central, on-premises data center. Fast forward 25 years to a time when application growth is unprecedented and enterprise applications run from a wide range of cloud endpoints - some public, some private, some via SaaS (Software as a Service) delivery, some managed by you, some managed by others and all seemingly mission-critical to the business. Welcome to the world of multi-cloud. Currently, every industry trend report identifies multi-cloud as a key strategy for most large organizations. However, this operating model brings a wide range of new security challenges that must be addressed by Information Security (InfoSec) leaders if this model is going to prove sustainable and secure.
Cloud environments are increasingly interconnected, making it difficult to maintain a secure perimeter. While this less walled-off approach has many advantages, it can also lead to security risks by increasing the potential attack surface. Ideal cloud security plans enable companies to take advantage of cloud computing benefits while also minimizing the risks.
Cloud computing creates a number of other unique security issues and challenges. For example, it is difficult to identify users when addresses and ports are assigned dynamically, and virtual machines are constantly being spun up. In addition, multitenant environments in public cloud environments mean that an organization’s data shares space with the data of other organizations. Thus, it is important for public cloud providers to keep tenants isolated.
Three Cloud Security best practices
There are core best practices enterprises can deploy to ensure cloud security, starting with ensuring visibility in the cloud architecture across the organization.
- Know who is responsible for each aspect of cloud security, rather than assuming that the cloud provider will handle everything.
- Understand how cloud architecture works to help avoid security holes due to misconfiguration.
- Implement the principle of least privilege. Assign appropriate permissions,
disable unused ports, and remove unnecessary services, processes, and instances. All of these can contribute to the attack surface and vulnerabilities.
Responsibility for cloud security is shared between cloud providers (which offer several security tools and services to customers) and the enterprise to which the data belongs. The security obstacles in a Multi-Cloud environment are many and varied. This solution guide will focus on four key areas in depth, endpoint security, workload security, network security, and cloud security posture. The solutions discussed here and provided by VMware, provide a strong and secure foundation for modern Multi-Cloud environments.

At an architectural level, utilizing VMware Carbon Black, NSX, and Cloud Health Secure State, VMware can provide the following security capabilities across a Multi-Cloud environment.

Endpoint - VMware Carbon Black Cloud
Consolidated endpoint security, simplified
At VMware, we understand the current state of endpoint security and have built a solution that is uniquely positioned to meet today’s needs.
VMware Carbon Black Cloud™ is a cloud-native endpoint protection platform (EPP) that combines the intelligent system hardening and behavioral prevention needed to keep emerging threats at bay, using a single lightweight sensor and an easy-to-use console. Instead of needing to deploy a variety of products each with its own setups, configurations, and policies, this solution delivers multiple security capabilities through a common cloud-delivered platform that shares one sensor, one cloud console, and one dataset. As requirements change, adding new services is fast and easy, eliminating the need for additional Capex investment or the need to deploy new agents.
The platform is built on a comprehensive endpoint dataset that can be used and shared across tools and services—whether provided by VMware or other vendors. This creates a single source of truth and adds context to security across the board. This platform was constructed with the understanding that security needs grow and change as the threat landscape evolves.
Our differentiator: Behavioral analytics
A surveillance camera on the endpoint
At VMware, we focus on understanding attackers’ behavior patterns, enabling us to detect and stop never-before-seen attacks in real-time. How can a fileless attack be prevented without understanding the way it was executed? How can something previously unseen be recognized with only historical attack data? To provide the best security, it is important to understand how attackers operate. This is why behavioral analysis is at the foundation of everything we do. To enable this analysis, we collect comprehensive endpoint data. Rich data—and the deep visibility it provides—is the foundation of strong endpoint security. VMware Carbon Black Cloud is unique. Most endpoint security solutions begin recording data only when they determine an activity is suspect. This approach often misses earlier activities that are essential to determining the root cause. When a problem arises, whether it is with endpoint security or IT hygiene, it is difficult to rapidly investigate the issue, or gain insight into new attack patterns. In contrast, this platform continuously looks at endpoint activity, regardless of if it seems good or bad, and analyzes the behaviors. This gives security professionals the context and confidence they need to defend their systems. VMware has spent the better part of a decade developing and refining the ability to reliably collect, cost-effectively analyze and securely store massive amounts of data, without disrupting the network. Leveraging the power of the cloud, we can analyze more than 200 terabytes of endpoint data and more than 500 billion security events on a daily basis—that is 13 times the number of iMessages processed and 150 times the number of Google searches in the same period. These powerful analytics give power to the many endpoint security services offered on the cloud-native platform.
Our differentiator: Superior protection
Stop more attacks, take back control over endpoints and worry less
Our unique approach provides an advantage when it comes to protecting endpoints. By analyzing attackers’ behavior patterns, VMware Carbon Black Cloud can stop attacks, whether they have been seen before or not, and gives visibility into how these attacks evolved over time. This visibility allows us to detect new forms of attack, constantly evolve our security defenses, and deliver customizable control of security posture to our customers. In this way, organizations can future-proof themselves from adversaries who are constantly evolving their methods.
We achieve this by applying machine learning and behavioral models to analyze endpoint data and uncover malicious activity to stop all types of attacks before they reach critical systems. Streaming analytics is derived from event stream processing, a technique that has been implemented for years across multiple industries—from credit card fraud detection to high-frequency trading. By focusing on ongoing behavioral analysis as opposed to point-in-time detections, the platform can recognize when a series of actions that have taken place over time is suspicious. The platform stops both malware and non-malware attacks, including attacks that leverage known-good software to do malicious things. For example, an attack leveraging a command interpreter such as PowerShell to find and encrypt all files on the disk could be run entirely remotely without a file bypassing any form of signature-based prevention. However, the process running the commands would still exhibit behavioral patterns similar to ransomware, which would be detected and stopped. The platform threats, threats patterns, and indicators are invisible to traditional and machine learning antivirus by looking upstream to the root cause of attacks and then applying this knowledge to better predict future ones.
VMware Carbon Black Cloud offers out-of-the-box protection (for those who want to set it and forget it) and the option for highly customizable policies. This lets organizations disrupt future attacks by specifically addressing gaps or blind spots. IT and security professionals can create custom control policies for individual work groups in their environment, control update frequency, and define exactly what types of processes are or are not allowed to run, and how untrusted execution is handled. For example, unknown applications could be denied operation entirely or could be allowed to run but not allowed to make any network connections or invoke-command interpreters. This level of granular control ensures that professionals who need specific control of their machines can have it, while still stopping advanced attacks. When protecting endpoints, it is important to acknowledge that there are many ways to gather threat intelligence and utilize all available sources. More than 75 of the world’s leading incident response vendors use VMware Carbon Black to investigate breaches daily, providing insights into the most recent attacks. The dedicated VMware Carbon Black Threat Analysis Unit leverages these insights and further investigates current attack trends, ensuring our analytics are always up to date and evolving to protect against emerging attacks. On top of this, our customers have access to a user community of more than 30,000 security experts, allowing members to interact with one another and learn about the latest insights and intelligence.
Our differentiator: Actionable visibility
Cut down the guesswork and close security gaps, fast
VMware Carbon Black Cloud makes it possible to identify emerging threats, prioritize the most critical attacks, and provide detailed visibility into the attack chain to help professionals rapidly understand, investigate, and remediate attacks.
While siloed tool sets can make it difficult to fully understand what is happening on endpoints—forcing professionals to piece together the necessary information from multiple places—our platform gives a comprehensive picture of what occurred in the past and what is happening now. With the power of comprehensive IT, security professionals have deep visibility into the state of their endpoints—eliminating gaps and blind spots, accelerating investigations and remediation, and leading to a significant reduction in dwell time.
This visibility is beneficial to all security professionals and offers specific value to threat hunters and incident responders who need quick and clear access to data to investigate, proactively hunt for, and remediate threats. Our approach allows investigations that often take days or weeks to be completed in just minutes. The sophisticated detection capabilities combine custom and cloud-delivered threat intel, automated watchlist, and integration with the rest of the security stack to efficiently scale hunting across the enterprise.
The platform’s quick and agile search/zoom process, with trees and timelines, gives a comprehensive understanding of how an attack was executed. It is easy to uncover exactly where an attacker went and what they did, as well as the root cause, in minutes to quickly address gaps in defenses. With remote investigation and remediation of any endpoint from anywhere, security professionals can reduce IT involvement, eliminating unnecessary reimaging and support tickets.
To augment and supplement the operating system event data that it is continuously collecting, the platform offers tools to gather additional information that cannot and should not be collected on a continuous basis. Real-time audit and remediation capabilities make it faster and easier for security and IT teams to assess and change system states to harden their environment against the most relevant threats. This power to create custom queries provides visibility into precise details about the current state of all devices and workloads—on and off the network. Professionals can then respond to this information by isolating infected systems to prevent lateral movement, creating a remote secure shell to any endpoint, collecting, and storing additional forensics data for post-incident investigation, or running scripts for full remediation.
Administrators also have the option to run queries against specific groups of devices and even individual devices. This enables the user to start broadly and then get more granular by targeting only those machines important to that specific investigation or audit.
Having the tools to quickly gather all the information needed to fully understand an attack and being able to take immediate action remotely helps professionals reduce dwell time and minimize risk in their environment.
Our differentiator: Simplified operations

Eliminate multi-vendor complexity and agent fatigue
While most endpoint security programs require multiple siloed systems that burden end users and complicate management, VMware Carbon Black Cloud provides a single consolidated platform, supporting multiple endpoint security needs. Although some AV (Anti Virus) vendors have begun to use cloud-based consoles, they aren’t taking full advantage of the cloud for security analysis and operations. Additionally, other vendors call themselves a “platform” but actually operate as a suite of separate products. Unlike these solutions, our cloud native platform delivers multiple services using a single lightweight sensor, enabling organizations to consolidate security products. A centralized, unified console provides professionals access to numerous capabilities and the complete dataset.
This platform makes it easy to deploy multiple security services without compromising endpoint performance. There is no need to purchase or stand-up onsite infrastructure, and our out-of-the-box policies are easily customized to fit any environment. Additionally, when an organization decides that it is time to expand their security capabilities, they can seamlessly add new features without new infrastructure sensors or deployment costs.
VMware Carbon Black Cloud automatically adapts to new attacks, so endpoints remain protected without requiring manual updates. Gone is the burden of constantly distributing large signature updates. Our automatic protection against the latest, most advanced threats gives organizations access to new and updated features as soon as they are released.
Strengthen security posture
When security tools can work together, they provide more visibility, more context and ultimately better overall protection. Unlike traditional solutions that exist in silos, our platform is an extensible platform built on open APIs, elegantly integrating with the rest of a company’s security stack. Pre-built integrations are available for many industry-leading solution providers such as IBM, Splunk, Exabeam, Sumo Logic, and more. This shared visibility drives a common understanding of issues across security and IT teams, decreasing friction and simplifying workflows. Security and IT professionals can extract more value from their data by adding context that other solutions lack. Access to unfiltered data speeds up investigation and analysis, leading to identification and remediation of more attacks.
For example, the tight integration with IBM QRadar allows administrators to leverage industry-leading next-generation antivirus (NGAV) and endpoint detection and response (EDR) solutions to see, detect and act on endpoint activity from directly within the QRadar console. When necessary, security analysts are able to immediately remediate at the point of compromise from the QRadar console, streamlining workflows and speeding response.
Beyond integrations, data collected from the endpoint can be exported quickly out of the platform’s data pipeline for use with customer-specific integrations and custom processing. Open APIs further allow organizations to build custom dashboards for integrated management and reporting and create new workflows that support and enhance their security programs. When security tools are operationally unified, an organization’s overall security posture can improve dramatically, reducing dwell time and risk.
Services delivered through VMware Carbon Black Cloud
NGAV and behavioral EDR
The VMware Carbon Black NGAV and behavioral EDR solution use machine learning and behavioral models to analyze endpoint data and uncover malicious activity to stop all types of attacks before they reach critical systems.
VMware offers powerful, flexible prevention that is able to stop malware ransomware and non-malware attacks. It prevents these attacks automatically, whether the endpoint is online or offline, from anywhere in the world, and is able to keep up with the always-changing threat landscape to block emerging never-before-seen attacks that other solutions may miss. VMware’s industry-leading detection and response capabilities reveal threat activity in real-time, so organizations can respond to any type of attack as soon as it’s identified. The root cause of an attack can be uncovered in minutes through visualizations that show every stage of the attack with easy-to-follow attack chain details. VMware Carbon Black Cloud Endpoint™ Standard lets administrators immediately triage alerts by isolating endpoints, deny listing applications, or terminating processes. Professionals can secure shell into any endpoint on or off the network to perform full investigations and recommendations remotely.
Alert monitoring and triage
The VMware Carbon Black managed alert monitoring and triage service provides customers with a world-class professional team of VMware security experts who work side by side with organizations that need more resources to validate and prioritize alerts, uncover new threats, and accelerate investigations.
The VMware U.S.-based experts analyze, validate and prioritize alerts from VMware Carbon Black Cloud, helping to ensure that companies do not miss the threats that matter. The service provides additional, human-generated context to alerts, such as connecting alerts caused by the same root cause, to help streamline investigations and resolve security issues. VMware threat experts proactively identify trends by monitoring threat activity across millions of endpoints, providing advice on widespread attacks and retroactively detecting and confirming emerging threats based on iterative discovery techniques. Monthly reports summarize alert data, turning a month’s worth of unfiltered data into actionable recommendations that help security professionals see the bigger picture and continually improve efficacy.
Enterprise EDR
VMware Carbon Black® Cloud Enterprise EDR,™ our threat hunting and incident response (IR) solution, delivers continuous visibility for top security operations centers and IR professionals.
Investigations that typically take days or weeks can be completed in just minutes. Carbon Black Cloud Enterprise EDR correlates and visualizes comprehensive information about endpoint events, giving IT and security professionals greater visibility into their environments. The solution’s sophisticated detection enables indicators of compromise (IoC) monitoring with your choice of threat intel, including your own custom feeds. This solution extends the automated recognition of tactics, techniques, and procedures (TTPs) in Carbon Black Cloud Endpoint Standard with deep investigation data and tools to help understand current attacks as well as longer-term attack patterns. With threat hunting on the VMware Carbon Black Cloud, professionals have the power to respond and remediate in real-time, stopping active attacks and repairing the damage quickly.
Audit and remediation
VMware Carbon Black® Cloud Audit and Remediation,™ our real-time assessment and remediation solution, enables security and IT teams to assess and change system states to harden their environment against the most relevant threats. This allows teams to effortlessly benchmark their devices, workloads, and containers against industry standards or regulations from a single console to help minimize risk and simplify operational reporting across the entire fleet.
Carbon Black Cloud Audit and Remediation gives administrators visibility into the most precise details about the current state of all endpoints. It automates operational reporting on patch levels and assesses IT hygiene. When combined with the VMware threat hunting capabilities, Carbon Black Cloud Audit and Remediation provides an unprecedented level of visibility to speed investigation and threat hunting.
Workload – VMware Carbon Black Workload
Advanced workload protection for the modern data center
As organizations continue their journey toward cloud transformation and application modernization, they require modern security solutions that are both powerful and easy to operationalize. VMware Carbon Black Workload™ delivers advanced protection purpose-built for securing modern workloads to reduce the attack surface and strengthen security posture. This innovative solution combines prioritized vulnerability reporting and foundational workload hardening with industry-leading prevention, detection, and response capabilities to protect workloads running in virtualized, private and hybrid cloud environments.
Tightly integrated with VMware vSphere, VMware Carbon Black Workload provides advanced security that alleviates installation and management overhead and consolidates the collection of telemetry for multiple workload security use cases. This unified solution enables security and infrastructure teams to automatically secure new and existing workloads at every point in the security lifecycle while simplifying operations and consolidating the IT and security stack.
Identify risk and harden workloads
VMware Carbon Black Workload helps security and infrastructure teams focus on the most high-risk vulnerabilities and common exploits across their environments. It’s not about finding the most vulnerabilities—it’s about finding the right ones. Prioritize vulnerabilities based on a combination of the Common Vulnerability Scoring System (CVSS), real-life exploitability, and frequency of attack, and increase patching efficiency with best-in-class prioritization. The real-time vulnerability assessment helps security and infrastructure teams understand vulnerability context with risk scores and links to the National Vulnerability Database, and eliminates the need for resource-heavy scans, with no additional administrative overhead or setup. VMware Carbon Black also provides visibility into operations hygiene; indicators of compromise (IOCs); malicious tactics, techniques, and procedures (TTPs); and ordinary events that occur in the system.
vSphere administrators can easily activate workload protection as a feature right from the vSphere Client, with bulk enablement and lifecycle management for virtual machine inventory. The vSphere dashboard provides visibility into appliance health, inventory status, and install workflow, and allows the infrastructure team to see a risk-prioritized list of operating system and application vulnerabilities found across the environment. VMware Carbon Black Cloud Workload enables deeper, unparalleled visibility into your environment to reduce risk and harden workloads while helping to streamline and operationalize security.
Prevent, detect, and respond to advanced attacks
Security teams often lack visibility and control in highly dynamic, virtualized data center environments. VMware Carbon Black Workload protects workloads running in these environments by combining foundational vulnerability assessment and workload hardening with industry-leading NGAV, workload behavioral monitoring, and EDR for workloads.
With advanced workload protection from VMware, the security team can analyze attacker behavior patterns over time to detect and stop never-seen-before attacks, including those manipulating known-good software. If an attacker bypasses perimeter defenses, VMware Carbon Black empowers security teams to shut down the attack before it escalates to a data breach. By embedding security into the infrastructure, you can easily audit the current system state to track security posture and harden workloads, while enabling easier collaboration with vSphere administrators to address known vulnerabilities.
Simplify operations for IT and security teams
At VMware, we take an intrinsic approach to delivering security—building it into the infrastructure everywhere workloads are deployed. Through this unique approach, we can eliminate the trade-off between security and operational simplicity by providing a single source of truth for infrastructure and security teams to accelerate response to critical vulnerabilities and attacks, while enabling collaboration and reducing friction. Simplify and consolidate your IT and security stack by replacing multiple point security tools that compete for resources with VMware Carbon Black.
VMware Carbon Black Cloud Workload Capabilities
Security is all about bringing the right data at the right time to the right user, all in a consistent and actionable fashion. VMware Carbon Black Cloud Workload is a testament to our Intrinsic security vision. We are delivering features that give the Security Analyst unprecedented insight into workloads, and we are also giving the vSphere Admin faster and easier access to the data necessary to identify risk, harden systems, and reduce the attack surface.
For Security Teams
For the security professional, VMware Carbon Black Cloud Workload provides visibility into areas that are traditionally hard to secure. Business-critical applications are often mission-critical, and security can often be overlooked when critical business operations might be impacted. Virtualized systems are “hard to see into” and you won’t often get rights to log into virtualized machines or the virtualization infrastructure to perform vulnerability scans, or even receive security alerts from NGAV or EDR products. With VMware Carbon Black Cloud Workload, you will have:
Full Visibility into Workload Inventory and Security Coverage
See a complete inventory of all workloads operating within an ESXi platform. For the first time, you will get to see what servers are on (or off) without having to ask your IT Administrator or Application Administrator. In addition to the inventory, you can quickly identify which workloads are protected by Carbon Black’s NGAV and/or EDR functions and which ones are not. In addition, you can work with the vSphere Admin on a shared view allowing you to coordinate coverage and/or compensating controls where you need them. Not only do you see all the systems, but you can also quickly see when new ones are deployed or powered on!
Risk-Prioritized Vulnerability Data
Touchless access to vulnerability data for the operating system and key applications across server systems. Just by deploying VMware Carbon Black Cloud Workload, you will see a prioritized list of CVEs (Common Vulnerabilities and Exploits) that is updated with a no-touch, incredibly low-impact data collection. The best part is that we have partnered with Kenna Security to integrate their unique data science-based approach to risk prioritization. Now you can identify the true risk of every cloud workload, with easy-to-understand risk scores and detailed intelligence that allows you focus on the vulnerabilities that matter, remediate faster, and align the entire business around a common objective.
Workload Audit and Remediation
Live query functionality from the Carbon Black Cloud allows teams to interrogate the current status of workloads at scale to track security posture, maintain IT hygiene, and report on compliance. With the ability to gather more than 2,000 artifacts on-demand or on a scheduled basis, teams can easily monitor drift and take immediate action remotely to proactively reduce the attack surface on critical workloads.
Workload Behavioral Monitoring with NGAV and EDR for Workloads
Depending on your organization’s security requirements, you will also have access to our industry leading NGAV and Enterprise EDR functionality for your workloads. Whether you want to replace legacy antivirus slowing down your servers, or gather and analyze extensive security data, you can leverage the full set of VMware Carbon Black security capabilities on your workloads.
For Infrastructure Teams
For the vSphere Administrator, the focus shifts to more operational and administrative concerns. Fortunately, we have you covered also, with:
Simple Deployment
Setting up VMware Carbon Black Cloud Workload on a vSphere instance can take as little as fifteen minutes. Installing Carbon Black Workload Appliance in under 15 minutes We leverage the same technology you are used to using for other plugins such as NSX or vCenter itself. Deploy the Carbon Black Cloud Workload appliance, connect to the Carbon Black Cloud console, enter a few critical configuration parameters and you are ready to go!
Lightweight Sensor Lifecycle Management
The same inventory view available to the security administrator is built into the vCenter plugin. As a vSphere Admin, you can see your inventory and quickly identify which workloads are protected and which ones are not. Through the power of VM Tools, you can enable security on any workload and in bulk or perform upgrades.
Risk-Prioritized Vulnerability Assessment
The bane of vulnerability management is that the group responsible for patching is rarely the same group looking at the security impact of vulnerabilities. Classic scanner data rapidly gets out of sync, ticketing systems are slow, and it is hard to get a common view between the security team, the vulnerability management team, and the IT team. Through the vCenter plugin, you get the same data as the security team and can either work to apply patches by priority or take alternate measures such as powering down non-critical but vulnerable systems. A shared view of the data leads to faster resolution!
VMware Carbon Black Workload Architecture
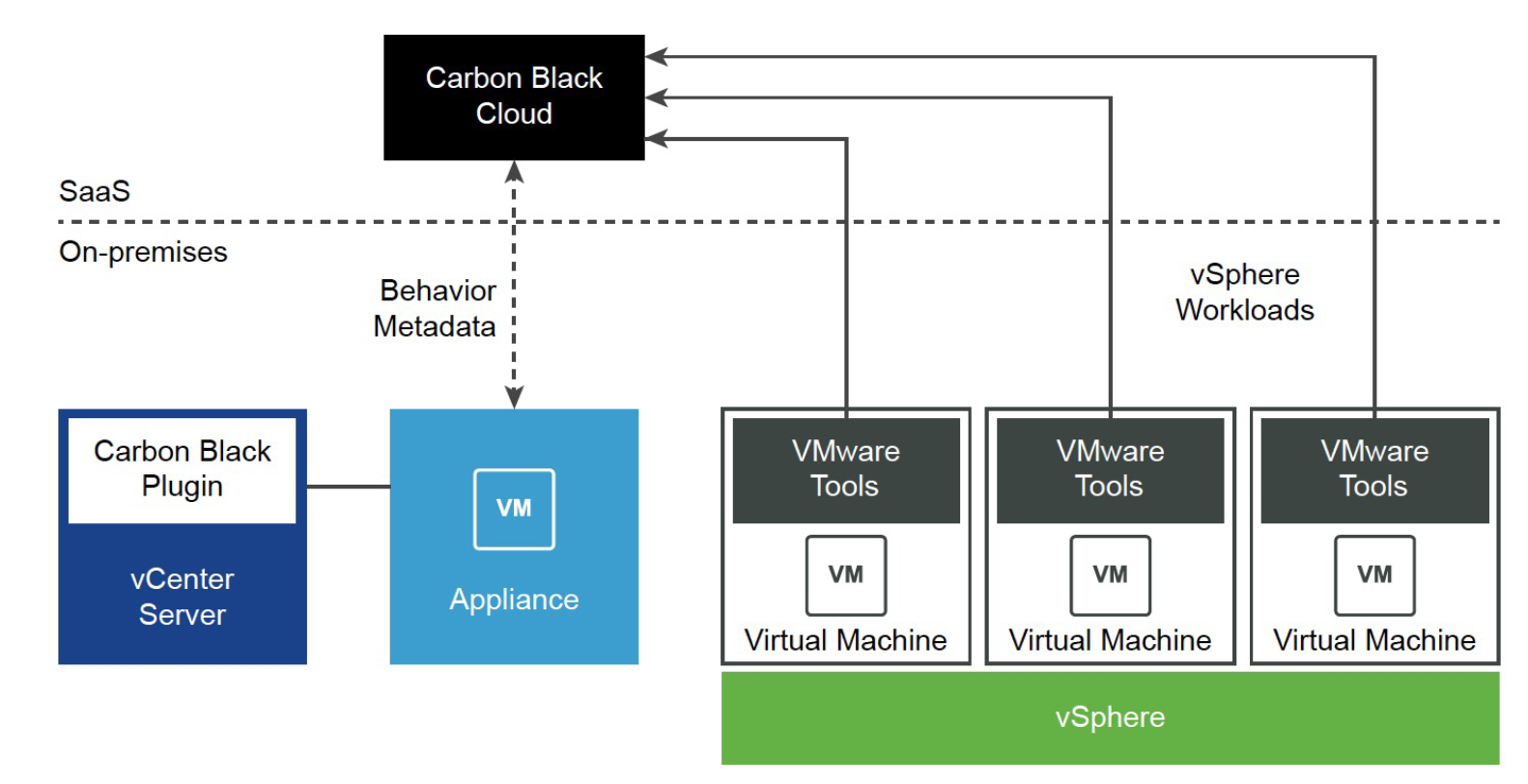
Carbon Black's sensor launching capability is packaged in VMware Tools 11.2.0 and later versions. This determines the eligibility of Windows virtual machines for Carbon Black protection and facilitates the sensor delivery with a single-click and no disruption to any business operations.
vCenter Plugin
Carbon Black plugin can be accessed using the vSphere Client. This provides the capability to the vSphere Admin to enable/disable Carbon Black on eligible workloads and access protection services such as Inventory, Lifecycle Management, Vulnerability Assessment.
Sensor Deployment Experience
Users can easily enable Carbon Black protection on eligible virtual machines with a single click from the Carbon Black Console and vSphere Client. After Carbon Black protection is enabled, there is no need to reboot the virtual machine. This eliminates the burden of deploying an additional agent and disrupting any business operations. This experience is supported on Windows and Linux virtual machines independent of domain membership.
Inventory
InfoSec admin and vSphere admin can easily view the inventory of the virtual machines using the Carbon Black Console and vSphere Client. They can easily learn about its protection status and assigned policies. With a single click, they can get access to a richer data set about virtual machines including their vulnerabilities and trigger various management actions.
Lifecycle Management
InfoSec admin and vSphere admin can easily enable/disable/upgrade Carbon Black sensor on the virtual machines. With a single click, they can enable/disable/update Carbon Black sensor on one or multiple virtual machines. InfoSec admin can even perform additional actions such as assigning policy, enable/disable bypass, query assets, etc. on one or multiple virtual machines using the Carbon Black Cloud console.
Vulnerability Assessment
VMware Carbon Black Cloud Workload provides InfoSec and vSphere admins with a list of OS (Operating System) and Application vulnerabilities across protected virtual machines. This solution is scan-less and risk-prioritized to reduce operational overhead and to provide the most critical data to you in an easy-to-consume format. This allows the InfoSec and vSphere admin teams to utilize a single source of truth for vulnerability assessments.
Network - NSX Security
Product Overview
In the same way that server virtualization programmatically creates and manages virtual machines, NSX-T Data Center network virtualization programmatically creates and manages virtual networks.
With network virtualization, the functional equivalent of a network hypervisor reproduces the complete set of Layer 2 through Layer 7 networking services (for example, switching, routing, access control, firewalling, QoS) in software. As a result, these services can be programmatically assembled in any arbitrary combination to produce unique, isolated virtual networks in a matter of seconds.
VMware NSX-T builds security into the network virtualization infrastructure. There are many built-in services that are part of NSX-T that enhance security. Security teams can protect the data center traffic across virtual, physical, containerized, and cloud workloads. The security capabilities are always present in the infrastructure and are quickly configurable. Further, no one can tamper with the security controls because they reside in the hypervisor, effectively decoupling the controls from your workloads.
VMware NSX Introduction
VMware NSX® is the network virtualization and security platform that enables VMware’s cloud networking solution with a software-defined approach to networking that extends across data centers, clouds, and application frameworks. With NSX, networking and security are brought closer to the application wherever it’s running, from virtual machines (VMs) to containers to physical servers. Like the operational model of VMs, networks can be provisioned and managed independent of the underlying hardware. NSX reproduces the entire network model in software, enabling any network topology—from simple to complex multitier networks—to be created and provisioned in seconds. Users can create multiple virtual networks with diverse requirements, leveraging a combination of the services offered via NSX or from a broad ecosystem of third-party integrations—ranging from next-generation firewalls to performance management solutions—to build inherently more agile and secure environments. These services can then be extended to a variety of endpoints within and across clouds.

NSX Architecture
NSX-T has a distributed architecture. Security enforcement controls are located at the virtual network interface of each workload and provide a granular mechanism to police traffic flows. There is no centralized appliance that limits security capacity, and you do not need to artificially hairpin the network traffic to a network security stack. As NSX-T is integrated into the virtualization infrastructure, it has visibility into all applications and workloads. NSX-T uses this visibility to derive rich application context, closely track the life cycle of workloads and automate security policy management.
NSX Distributed Firewall
NSX Distributed Firewall (DFW) is a distributed, scale-out internal firewall that protects all East-West traffic across all workloads without network changes, thereby radically simplifying the security deployment model. It includes a stateful L4-L7 firewall, an intrusion detection/prevention system (IDS/IPS), a network sandbox, and behavior-based network traffic analysis. With the NSX Firewall, you can protect the data center traffic across virtual, physical, containerized, and cloud workloads from internal threats and avoid damage from threats that make it past the network perimeter.
You can use NSX-T Distributed Firewall (DFW) for Macro-Segmentation (Security Zones) and Micro-Segmentation. Distributed Firewall provides complete L2-L7 East-West visibility and enforcement, with automated policy formulation. It works on both Physical Servers and VMs on ESXi and Physical Network changes are not required. By using DFW, it is possible to segment in any matter desired. There are four basic types of segmentation, many of which can coexist – each applied in different sections of the environment.
- Zone Segmentation: Zone Segmentation can be as general as segmenting production from non-production, or it may be a far more detailed segmentation by business unit, function, or product offering. The point is that each zone is defined independently of segments, VLANs, data centers, or other constructs. Zones are entirely logical definitions that can be used to define security policy.
- VLAN Segmentation: VLAN segmentation is most used when replacing the legacy firewall infrastructure. In this model, an IP segment is a defining element for a source or destination of the security policy.
- Application Segmentation: Application segmentation is used to define a logical security ring around an application. Because applications are not frequently understood in detail, it can be convenient to simply define a tag for a given application and apply this tag to all its components and allow full communication between said elements. This brings greater security than a large zone definition which can have multiple applications, without requiring detailed understanding for micro-segmentation.
- Micro-Segmentation: Micro-segmentation is a security model where communication between elements is defined as explicitly as possible. At its extreme, micro-segmentation can be the explicit definition of communication between pairwise elements. Clearly, this is operationally complex, thus NSX offers micro-segmentation based on tags that allow explicit definition by groups. For example, you can define a rule which allows SSL (Secure Socket Layer) but only TLS (Transport Layer Security) version 1.3 to the tagged secure web servers. Based on the needs of your organization, you can segment traffic in each of these different manners.
With NSX-T, all these segmentation approaches are not exclusive but can coexist. You can decide to segment a lab in a zone model by just setting up a boundary around it and a DMZ environment in a micro-segmentation. You can segment non-production environments just by applications whereas you can further segment the production applications containing sensitive customer data using VLAN. The change of one security model to another is accomplished through a simple policy push, without the need to re-architect any networking infrastructure.
NSX Gateway Firewall
NSX Gateway Firewall is instantiated per gateway and is supported at both Tier-0 and Tier-1. Gateway firewall works independently of NSX-T DFW from a policy configuration and enforcement perspective, although you can share objects from the DFW.
You can use NSX-T Gateway Firewall to provide firewalling for the North-South traffic at the Layer 3 boundary. You can use the Gateway Firewall as an inter-tenant/zone firewall from the north-south perspective, along with the Distributed Firewall. Gateway Firewall is supported on both Tier-0 and Tier-1 gateways. Tier-0 supports basic L3/L4 stateful firewall, whereas Tier-1 supports basic L3/L4 and advanced L7 features like L7 Application ID, URL filtering, IDS/IPS, TLS Inspection, Identity Firewall, and Malware Prevention. The Gateway Firewall provides firewalling services and other services that cannot be distributed such as NAT, DHCP, VPN, and load balancing, and needs the services router component of the gateway.
NSX Intelligence
NSX Intelligence, a security analytics and policy management solution, automatically determines the communication patterns across all types of workloads, makes security policy recommendations based on those patterns, and checks that traffic flows to conform to the deployed policies.
NSX Advanced Threat Prevention (ATP)
NSX Advanced Threat Prevention is a suite of analysis tools designed to defend against advanced threats that use known and unknown attack vectors. ATP augments more common security solutions aimed at repelling known intrusion strategies.
Key protection features include:
Malware Prevention detects and prevents malicious file transfers by using a combination of signature-based detections of known malware, including static and dynamic analysis of malware samples. You can configure Malware Prevention on your gateway firewall for North-South traffic. For East-West traffic, it can be configured in distributed Intrusion Detection and Prevention System (IDPS), utilizing Guest Introspection to protect virtual machines (VMs).
Network Detection and Response (NDR) collects the traffic from the entire network infrastructure across on-premises, cloud, and hybrid cloud. It uses AI (Artificial Intelligence) techniques to analyze traffic and gain insights about advanced threats. With NDR, you can visualize the entire traffic flow, which is correlated and presented as campaign cards along with affected hosts and a detailed timeline of threats. Additionally, NDR maps to the MITRE ATT&CK tactics and techniques for resourceful understanding of key events in the campaign.
Benefits of NSX Advanced Threat Prevention
By incorporating a leading ATP solution into your security stack, you harness three critical advantages:
- Maximum Network Threat Visibility: In using multiple threat detection techniques at once (IDS/IPS, NTA, Network Sandbox, etc.), ATP delivers deep visibility into all your network traffic.
- Advanced Malware Detection: ATP helps secure both Private and Public Cloud workloads against threats that have been engineered to evade standard security tools.
- Lower False Positives: ATP can greatly improve the accuracy of your alerts, which means your security teams can focus on a smaller set of actual intrusions.
Workloads
Workloads come in various form factors like virtual machines, containers, and physical servers. In addition, workloads are hosted in different environments like on-premises, native cloud, or managed cloud. The heterogeneity of the workload form factor and deployment type further challenges the organizations regarding security coverage, policy consistency, number of platforms to be managed, and overall operational simplicity. The requirement of an organization is to have an operationally simple platform that provides consistent policy across virtual machines, containers, physical servers, and native cloud workloads without compromising the application and data security.
Key Advantages for NSX in a Multi-Cloud environment:
- Complete network security coverage across all traffic flows and workload types
- Analyze advanced threats with full-system emulation sandbox
- Easily create, enforce, and manage granular micro-segmentation policies to secure the East-West
- Network quarantine infected guests preventing lateral movement
- Flow visualization to understand malicious traffic and activity
Additional Resources
NSX TechZone Security Resources: https://nsx.techzone.vmware.com/security-resources
Cloud Security Posture - CloudHealth Secure State
Product Overview
Reducing misconfigurations, monitoring malicious activity, and preventing unauthorized access are foundational activities necessary to ensure security and compliance of applications and data in the cloud. As criminals become more sophisticated in their abilities to exploit cloud misconfiguration vulnerabilities, security teams need a smarter approach to prevent security breaches.
CloudHealth Secure State is an intelligent cloud security and compliance monitoring platform that helps organizations reduce risk and protect millions of cloud resources by remediating security violations and scaling best practices at cloud speed.
Introduction to CloudHealth Secure State
Improve Visibility
Gain Real-Time Visibility Across Cloud & Kubernetes Infrastructure
Monitor multiple cloud providers and understand how a minor configuration change can elevate risk across connected cloud objects
- Quickly discover inventory, explore cloud topology, and drive investigations with a unified search engine for multiple cloud providers, regions, and accounts
- Detect security risks within seconds and monitor ephemeral cloud resources with an event-based approach that minimizes API calls to cloud
- In a single graph view, get deep security context including cloud resource relationships, misconfigurations, threats, metadata, and change activity
- Audit configuration changes and track progress developers make in resolving security and compliance violations across the organization and sub-projects

Define Governance Standards
Establish Security and Compliance Best Practices
Build cloud security and compliance program to establish organization-wide standards and fine-tune policies
- Assess misconfiguration and compliance risk by automating benchmarks such as CIS, GDPR, HIPAA, ISO 27001, MITRE ATT&CK Cloud, NIST, PCI, & SOC 2
- Eliminate security and compliance blind spots by defining custom frameworks and rules specific to technical needs
- Reduce false positives and allow exceptions to security policies by automatically suppressing rules or findings based on pre-defined criteria
- Prioritize security of most vulnerable cloud resources with an intelligent risk-scoring algorithm that makes it easy to identify critical findings

Remediate Violations
Resolve Violations with a Secure Auto-Remediation Framework
Use automation to improve security and compliance posture and build guardrails that prevent mistakes
-
Safely embrace auto-remediation with a framework that takes actions without writing permissions to a customer cloud environment
-
Mitigate risks at scale with a rich library of pre-defined remediation jobs and the ability to create custom jobs as code
-
Click to fix known violations and precisely target resources based on filtering criteria such as a cloud provider type, region, account, or tag
-
Proactively prevent mistakes by enabling guardrails that automatically resolve new violations that match specified filtering criteria

Increase Collaboration
Empower Developers and Streamline Security Operations
Automate cloud security operations in the company with an API-first platform that easily integrates with other IT, security, and developer tools
- Shift-left security to proactively identify and resolve violations through API based verification within CI / CD pipelines
- Enable developers to manage cloud risk with Role-Based Access Controls for monitoring security and compliance findings
- Prioritize security and incident response by correlating threats ingested from third-party sources with native security and compliance findings
- Streamline SOC investigations by easily exporting native findings for additional analytics in Security Information & Event Management systems

Key Advantages for Multi-Cloud:
Mitigate security and compliance risk with real-time security insights, CloudHealth Secure State does provide the following capabilities to help secure Multi-Cloud:
- Improve security visibility with real-time inventory search and investigation capabilities for multi-cloud environments.
- Reduce misconfigurations and prioritize threats with visual risk context and a more secure auto remediation approach.
- Benchmark compliance with industry standards with over 950 out-of-the-box rules and enterprise customizations.
- Plan how to operationalize your cloud security program through better collaboration between dev
- elopers, security, and operations team
Additional Resources
- VMware CloudHealth Product Page: https://cloudhealth.vmware.com/
- VMware CloudHealth HOL (Hands-On Lab): https://labs.hol.vmware.com/HOL/catalogs/lab/10903
Summary and Additional Resources
Summary
Discover how VMware Security Solutions address Multi-Cloud protection.
Additional Resources
- Carbon Black TechZone: https://carbonblack.vmware.com/
- NSX TechZone Security Resources: https://nsx.techzone.vmware.com/security-resources
Changelog
The following updates were made to this guide:
|
Date |
Description of Changes |
|
5/25/2022 |
|
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware Carbon Black Technical Marketing techzone-sbu@vmware.com.



