Ransomware Defense in Depth Strategy - Best Practices for Building a Strong Prevention
Introduction
Cyberattacks increased significantly in 2020, and ransomware is one of the most recurring and devastating attacks. Criminal enterprises using ransomware have collected billions of dollars from infected companies and individuals. The average attack results in companies spending hundreds of thousands of dollars to recover. This cost increases when enterprises pay the ransom. Ransomware attacks typically do not focus on a single industry and are common across all enterprises across the globe. In the United States, the government is now considering enforcing fines for enterprises paying ransom to discourage the paying of ransom during a ransomware attack. This threat has done little to stop ransomware proliferation. With offerings such as ransomware as a service, it is easier to sabotage an organization by encrypting their systems and data, and deleting or encrypting the organization’s backups to negate an established recovery strategy.
All organizations must bolster their defenses against ransomware and other cyber attacks immediately. However, the security technology landscape is complex and presents many challenges in implementing a strong security practice. The VMware intrinsic security approach simplifies the toolsets and processes required to secure end-users, private clouds, and public clouds. Intrinsic security is a fundamentally different approach to securing businesses that unifies security and IT teams and empowers organizations with deep context and insights that accelerate how they identify risk and prevent, detect and respond to threats.
In this resource, VMware documents solutions by incorporating the National Institute of Standards and Technology (NIST) controls specific to protect, detect and respond to functions contained in the NIST Cybersecurity Framework. These controls are further detailed in the NIST SP 1800 series of documents that address data integrity. This paper uses a defense-in-depth approach and outlines the VMware components and solutions necessary to protect users working from anywhere as well as an organization’s resources in a private or public cloud.
What is Ransomware?
Ransomware is a type of malware that attempts to deny access to a user’s or organization’s data, usually by encrypting the data with a cryptographic key known only to the hacker who deployed the malware. The organization’s data is held hostage until the ransom is paid. Once ransomware enters a system, it begins encrypting files or complete file systems. It blocks user access until requests for payments, which are often displayed in warning messages, are fulfilled. Unfortunately, there is no guarantee that the cryptographic keys needed to break the encryption will be provided upon payment.
This malware typically enters through malicious downloads, email links, social network messages, and websites. More recently, ransomware has been distributed through aggressive worms and targeted brute force attacks against public-facing remote access services, such as the Remote Desktop Protocol (RDP). Once the end-user has executed the malicious content, which often masquerades as legitimate files, the encryption takes place, and a message is displayed demanding a ransom. The ransom note usually threatens permanently losing access to their data and publicly releasing the intellectual property or embarrassing content.
Numerous criminal enterprises using ransomware target companies, nonprofits, governments, and schools of all sizes. Some of the most prominent ransomware organizations are DoppelPaymer, Egregor/Maze, NetWalker, REvil, and Ryuk. While these criminal enterprises use various strains of ransomware, they have common attack vectors for compromise, such as brute force attempts at public-facing services including RDP, the exploitation of outdated public-facing web software, and known vulnerabilities that may have not been remediated
Ransomware distribution scenarios
This paper focuses on three specific ransomware scenarios and how VMware solutions protect, detect, and respond to attacks against end-user computing, private cloud, and multi-cloud environments.
Ransomware distributed through websites or email
While working from anywhere, a user mistakenly downloads ransomware from an external web server or a link in an email. When the user executes this malicious software, it generates a cryptographic key that is sent back to the external web server. The malware then utilizes a privilege escalation exploit to propagate across the network. The malicious software deletes local backups, shadow copies (Windows), and Time Machine backups (macOS); encrypts files on the machines to which it propagated; and demands payment in exchange for the decryption of these files.

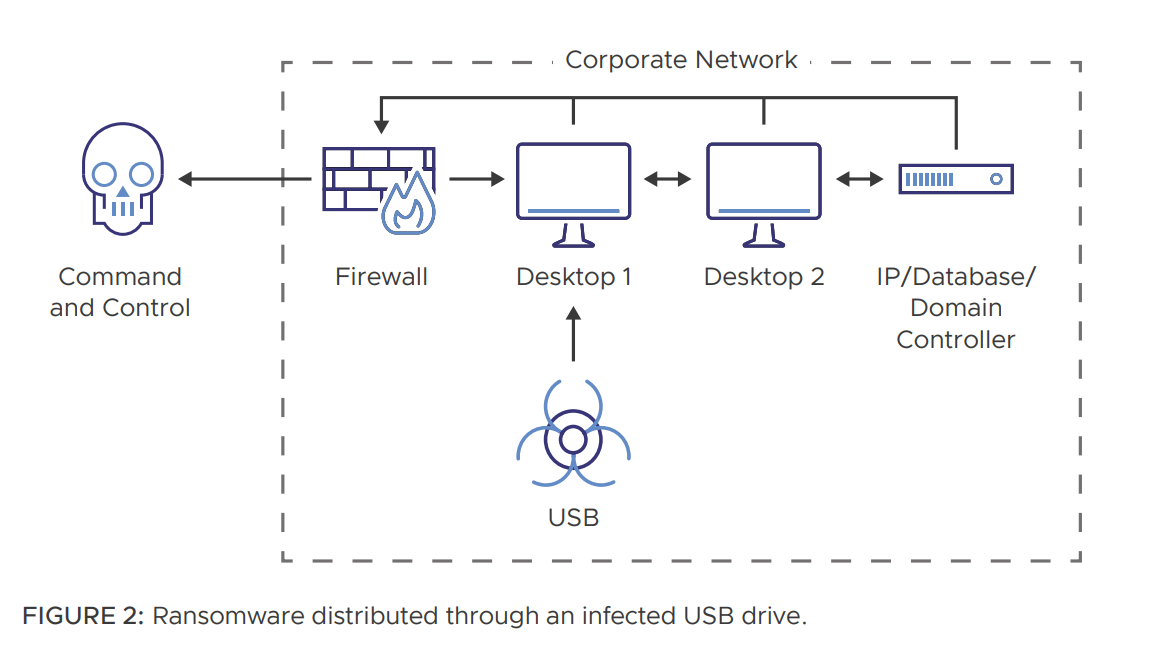
Ransomware distributed through an infected USB drive
A user finds an unmarked USB device and inserts it into their system. The USB device contains malicious software that may run automatically or with user interaction. The malicious software encrypts the
Ransomware distributed through a targeted attack
The actors obtain valid user credentials through a brute force attack on publicly accessible RDP. This user’s credentials are for a VMware administrator who has reused these credentials on multiple VMware vSphere® hosts. The attacker is able to enable a secure shell (SSH) on the vSphere hosts and upload ransomware to encrypt the VMDK files for all the virtual servers on these hosts. A ransom request is left on the vSphere hosts. The solutions sections in this paper are dedicated to a defense in depth strategy for end-user computing, private cloud, and multi-cloud environments. Ransomware propagating through websites or email, an infected USB drive, or a targeted attack is addressed in the End-user computing solutions section. If the attacker has gained access beyond end-users into a private or public cloud network, the capabilities documented will be necessary to protect, detect and respond to ransomware in the Private cloud solutions and Multi-cloud solutions sections.
The solutions sections in this paper are dedicated to a defense in depth strategy for end-user computing, private cloud, and multi-cloud environments. Ransomware propagating through websites or email, an infected USB drive, or a targeted attack is addressed in the End-user computing solutions section. If the attacker has gained access beyond end-users into a private or public cloud network, the capabilities documented will be necessary to protect, detect and respond to ransomware in the Private cloud solutions and Multi-cloud solutions sections.
NIST controls for ransomware
The VMware solutions in this paper follow the functions, categories, and subcategories documented in the NIST publications addressing data integrity:
- SP 1800-25 – Identifying and Protecting Assets Against Ransomware and Other Destructive Events
- SP 1800-26 – Detecting and Responding to Ransomware and Other Destructive Events
- SP 1800-11 – Recovering from Ransomware and Other Destructive Events These NIST publications do not focus solely on ransomware.
For the purposes of this paper, only the scenarios and controls specific to ransomware within these three publications are used in documenting ransomware-specific capabilities in VMware solutions.
The NIST approach to cybersecurity is documented in the NIST Cybersecurity Framework. The framework core contains five functions:
- Identify – develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
- Protect – develop and implement appropriate safeguards to ensure delivery of critical services.
- Detect – develop and implement appropriate activities to identify the occurrence of a cybersecurity incident.
- Respond – develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Recover – develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
To learn more about the framework, read the Framework for Improving Critical Infrastructure Cybersecurity. The following subsections specify the categories and subcategories in SP 1800-25, SP 1800-26, and SP 1800-11 supported by VMware solutions.
- Protect
-
Identity management, authentication, and access control:
• PR.AC-1 – Identities and credentials are issued, managed, verified, revoked, and audited for authorized devices, users, and processes
Data security:
• PR.DS-1 – Data-at-rest is protected
• PR.DS-6 – Integrity checking mechanisms are used to verify software, firmware, and information integrity Information protection, processes, and procedures:
• PR.IP-1 – A baseline configuration of information technology/industrial control systems is created and maintained incorporating security principles (e.g., the concept of least functionality)
• PR.IP-3 – Configuration change control processes are in place
• PR.IP-4 – Backups of information are conducted, maintained, and tested periodically
• PR.IP-9 – Response plans (Incident Response and Business Continuity) and recovery plans (Incident Recovery and Disaster Recovery) are in place and managed
Maintenance:
• PR.MA-1 – Maintenance and repair of organizational assets are performed and logged, with approved and controlled tools
• Protective technology:
• PR.PT-1 – Audit/log records are determined, documented, implemented, and reviewed in accordance with policy
- Detect
-
Anomalies and events:
• DE.AE-1 – A baseline of network operations and expected data flows for users and systems is established and managed
• DE.AE-2 – Detected events are analyzed to understand attack targets and methods
• DE.AE-3 – Event data are collected and correlated from multiple sources and sensors
• DE.AE-4 – Impact of events is determined
• DE.AE-5 – Incident alert thresholds are established
Security continuous monitoring:
• DE.CM-1 – The network is monitored to detect potential cybersecurity events
• DE.CM-3 – Personnel activity is monitored to detect potential cybersecurity events
• DE.CM-4 – Malicious code is detected
• DE.CM-5 – Unauthorized mobile code is detected
• DE.CM-7 – Monitoring for unauthorized personnel, connections, devices, and software is performed
Detection processes:
• DE.DP-2 – Detection activities comply with all applicable requirements
- Respond
-
Response planning:
• RS.RP-1 – Response plan is executed during or after an incident
Communications:
• RS.CO-2 – Incidents are reported consistent with established criteria Analysis:
• RS.AN-1 – Notifications from detection systems are investigated
• RS.AN-2 – The impact of the incident is understood
• RS.AN-3 – Forensics is performed
• RS.AN-4 – Incidents are categorized consistent with response plans
Mitigation:
• RS.MI-1 – Incidents are contained
• RS.MI-2 – Incidents are mitigated
• RS.MI-3 – Newly identified vulnerabilities are mitigated or documented as accepted risks
While the NIST publications do not directly address the recovery function for ransomware, VMware does provide a backup and recovery solution well-positioned to securely recover from a ransomware event. This solution is documented in the Multi-cloud solutions section. The ransomware capabilities in this paper should be implemented in addition to a complete cybersecurity defense in-depth approach. Defense in-depth best practices are documented in the next section.
VMware solutions for ransomware
Defense in depth
Defense in depth is defined as deploying multiple layers of defense across endpoints and public and private clouds to protect an organization from cybersecurity events. In this section, recommendations are documented on how to implement defense in depth to better secure organizations from ransomware attacks. While not specifically addressing the issue of ransomware, these recommendations for a defense in depth posture will provide a strong security foundation. It is recommended to follow these defense-in-depth best practices:
- Awareness and training program – End users are top targets. Everyone in the organization must be aware of the threat of ransomware and how it is delivered.
- Email scanning – Content scanning and email filtering should be used to detect threats before they reach end-users.
- Spam filters – These prevent phishing emails from reaching end users. Also, spam filters authenticate inbound emails using technologies such as Sender Policy Framework and DomainKeys Identified Mail.
- Block ads – Ransomware is often distributed through malicious ads served when visiting certain sites. Blocking ads can reduce that risk.
- Firewalls – These software or hardware appliances control network traffic through access or deny policies or rules. These rules include denylisting or allowlisting IP addresses, MAC addresses, and ports. There are also application-specific firewalls, such as web application firewalls (WAFs) and secure email gateways, that focus on detecting malicious activity directed at a particular application.
- Intrusion detection or prevention systems (IDS/IPS) – An IDS sends an alert when malicious network traffic is detected, whereas an IPS attempts to prevent and alert on identified malicious activity on the network or a user’s workstation. These solutions are based on the recognition of attacks on signatures of known malicious network activity.
- Endpoint detection and response (EDR) – This is software or agents that reside on the client system (e.g., a user’s laptop or mobile phone) and provide antivirus protection, alert, detection, analysis, threat triage, and threat intelligence capabilities. These solutions run on rulesets (i.e., signatures or firewall rules) or heuristics (i.e., detection of anomalous or malicious behaviors).
- Network segmentation – This is the practice of splitting a network into multiple subnetworks designed around business needs and technology requirements. This might include different sub-networks for executives, finance, operations, and human resources. Depending on the level of security required, these networks may not be able to communicate directly. Segmentation is often accomplished through the use of network switches or firewall rules.
- Inspect east-west internal traffic – This provides anomaly detection of certificates when traffic is encrypted.
- Inspect north-south traffic – This detects command and control (C&C) traffic by using threat intelligence to identify malicious IPs, domains, and more.
- Scan network artifacts – This dynamically analyzes file behaviors for threats by using AI to detect malicious code.
- Log aggregation – This collects logs from all critical devices, security controls, and endpoints in a central location for correlation and analysis.
- The principle of least privilege – This requires policy and technical controls to only assign users, systems, and processes access to resources (networks, systems, and files) that are absolutely necessary to perform their assigned function.
- Strong passwords – These are critical authentication mechanisms in information security. Modern password guidance involves using multifactor authentication for any account of value, using a phrase with multiple words, and not reusing passwords.
- Patch management – This is the process of applying updates to an operating system, software, hardware, or plug-in. Often, these patches address identified vulnerabilities that could allow cyberthreat actors unauthorized access to information systems or networks.
- Back up data regularly – This verifies the integrity of backups and tests the restoration process to ensure it’s working.
- Secure your offline backups – This ensures backups are not permanently connected to the computers and networks they are backing up.
- Conduct an annual penetration test and vulnerability assessment.
Summary
Summary Ransomware is a serious threat to all organizations across all industries. VMware provides many capabilities to protect organizations from ransomware attacks. If organizations are infiltrated, VMware technologies enable security operations to protect, detect and respond to these threats. Organizations must focus on deploying end-user solutions—such as Workspace ONE, Horizon, and VMware Carbon Black Cloud—to stop ransomware from entering the environment. vSphere, NSX, VMware Carbon Black Cloud, CloudHealth Secure State, VMware Tanzu, and vRealize Suite provide organizations with robust capabilities to protect against, detect and respond to ransomware in private and public clouds. These solutions must be deployed and configured as part of a larger defense in depth security model. Once VMware solutions are deployed and configured as documented in this paper, organizations will significantly reduce attack vectors and possess the tools and processes to protect, detect and respond quickly to ransomware events
Additional Resources
- Unexplored Territory Podcast: In episode 009, Preventing ransomware attacks with Carbon Black featuring Kendra Kendall we talk to focused on our Carbon Black offering and prevention of ransomware attacks in general. Kendra discusses how ransomware attacks work, and how you can leverage Carbon Black to develop a defense in depth strategy.
- Detecting and Rollback With Ransomware :
With VMware Carbon Black we need to ensure we are adapting for our customers as ransomware evolves. Utilizing Live Response Carbon Black Cloud can restore shadow copies by running the vssadmin command and then restoring using mlink on this particular device. Live Response is an extensible remote shell that can be used on Windows, MacOS or Linux, without the need for additional OS configuration. This tool is built into all Carbon Black Cloud products. Ransomware is pervasive, and as defenders, it is VMware’s responsibility to adapt and provide security that is future-ready. So in the case of rollback providing not only the ability to restore to a particular shadow copy, it is also providing disaster recovery tools to ensure business operations can resume as quickly as possible. Like to Learn more? Watch this Video
- Unlocking the Power of Security and Resiliency: Ransomware Protection DemoSecurity and resiliency are not the same thing, but they are a perfect combination. Watch this demo to understand how VMware Carbon Black Cloud and VMware Cloud Disaster Recovery work together to drive confidence in business growth through reliable, intelligent data protection.
Authors and Contributors
- Amanda Blevins
- Mandy Botsko-Wilson
- Niran Even-Chen
- Brian Heili
- Keith Luck
- Dale McKay
- Jon Nelson
- Adam Osterholt
- Scottie Ray
- Jeff Whitman
- James Murray
