Proofpoint with VMware Carbon Black Cloud
Proofpoint TAP
This is an integration between Proofpoint TAP and VMware Carbon Black Cloud (CBC). Depending on the configuration of Proofpoint TAP, users are able to access attachments while they're being analyzed by Proofpoint. If the attachment is found to be malicious, Proofpoint TRAP can remove the email from all corporate inboxes, however, if the attachment was downloaded prior to the email being deleted, the malicious file could still be present in the environment on end-user machines.
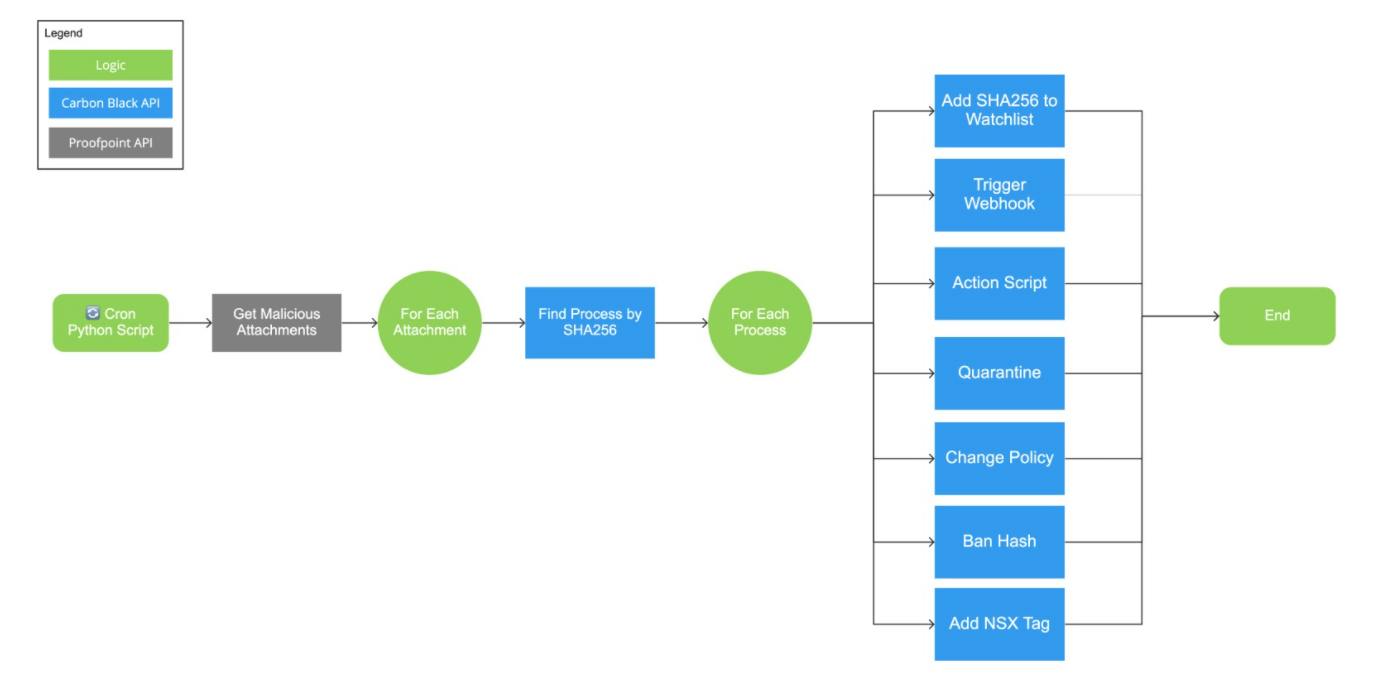
This integration will pull all email deliveries from x minutes ago (configurable, allows time for detonation, default 30) from Proofpoint TAP. For each attachment collected from Proofpoint, Carbon Black Cloud will search for any processes that match the malicious attachments' SHA256 hash value for a preset, custom time frame (up to 2 weeks). The process GUID's are stored in a local database to prevent duplication in searches and minimize API queries. Once the processes have been identified, the script will take action.
Action options consist of:
- Adding to a CBC Enterprise EDR Watchlist Feed
- Passing the SHA256, process information, and email information to a webhook
- Running a script (stops process/deletes file with CBC Live Response by default)
- Isolating the endpoint
- Moving the endpoint into a different or updated policy
How it Works
This is a flow diagram of how the integrations is designed:
Key Benefits
- Detect and stop advanced email threats
- Achieve multi-layered threat protection
- Secure organizations endpoints and data against sophisticated malware and malware-free attacks
Requirements
- Carbon Black Cloud Enterprise EDR
- Proofpoint TAP
- Python 3.x
Support
This is an open source, community supported integration posted to our community GitHub repo. Any issues should be submitted as an issue in GitHub, not a support ticket.
Enterprise EDR and Proofpoint Emerging Threats
This integration connects VMware Carbon Black Cloud Enterprise EDR with Proofpoint ET Intelligence Reputation List to provide visibility into the latest threats through a filterable Watchlist in the Carbon Black Cloud console. Using the command line arguments, a category (or feed) of IOCs from Proofpoint ET Intelligence Reputation List is pushed to a Watchlist in the Carbon Black Cloud. This Watchlist can be organized, filtered and alerted on based on severity and IOC type (IP or domain), and includes descriptions and tags for each IOC.
Requirements
- Carbon Black Cloud Enterprise EDR
- Proofpoint Emerging Threats
- Python 3.x
Support
This is an open source, community supported integration posted to our community GitHub repo. Any issues should be submitted as an issue in GitHub, not a support ticket.
Summary and Additional Resources
For more information, visit the Github repo for the the integrations below.
- Proofpoint TAP Connector for VMware Carbon Black Cloud
- VMware Carbon Black Cloud and Proofpoint ET Intelligence Reputation List Connector
Additional Resources

Changelog
The following updates were made to this guide:
|
Date |
Description of Changes |
|
2021/12/01 |
|
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware Security Business Unit Technical Marketing at SBU_tech_content_feedback@vmware.com .
