Carbon Black XDR - Technical Overview
Overview
Introduction
The technical Overview document provides a comprehensive understanding of Carbon Black XDR and its features, functionality, and architecture.
Audience
This document is intended for architects, developers, and other stakeholders. It provides information about Carbon Black XDR and how it can be used in an organization.
What is Carbon Black XDR
VMware Carbon Black Extended Detection and Response (XDR) is the latest evolution of security tools. VMware Carbon Black XDR extends endpoint detection and response by adding network and user telemetry, reducing blind spots across these domains and enabling security operations teams to visualize and analyze endpoint, workload, network and user data in context.
Carbon Black XDR offers a significant improvement on telemetry visibility from a single pane of glass, combining the SOC and NOC and providing the complete visibility required to get the highest confidence level in the response actions taken across the environment. Ultimately reducing Mean Time To Detection (MTTD) and Mean Time To Response (MTTR).
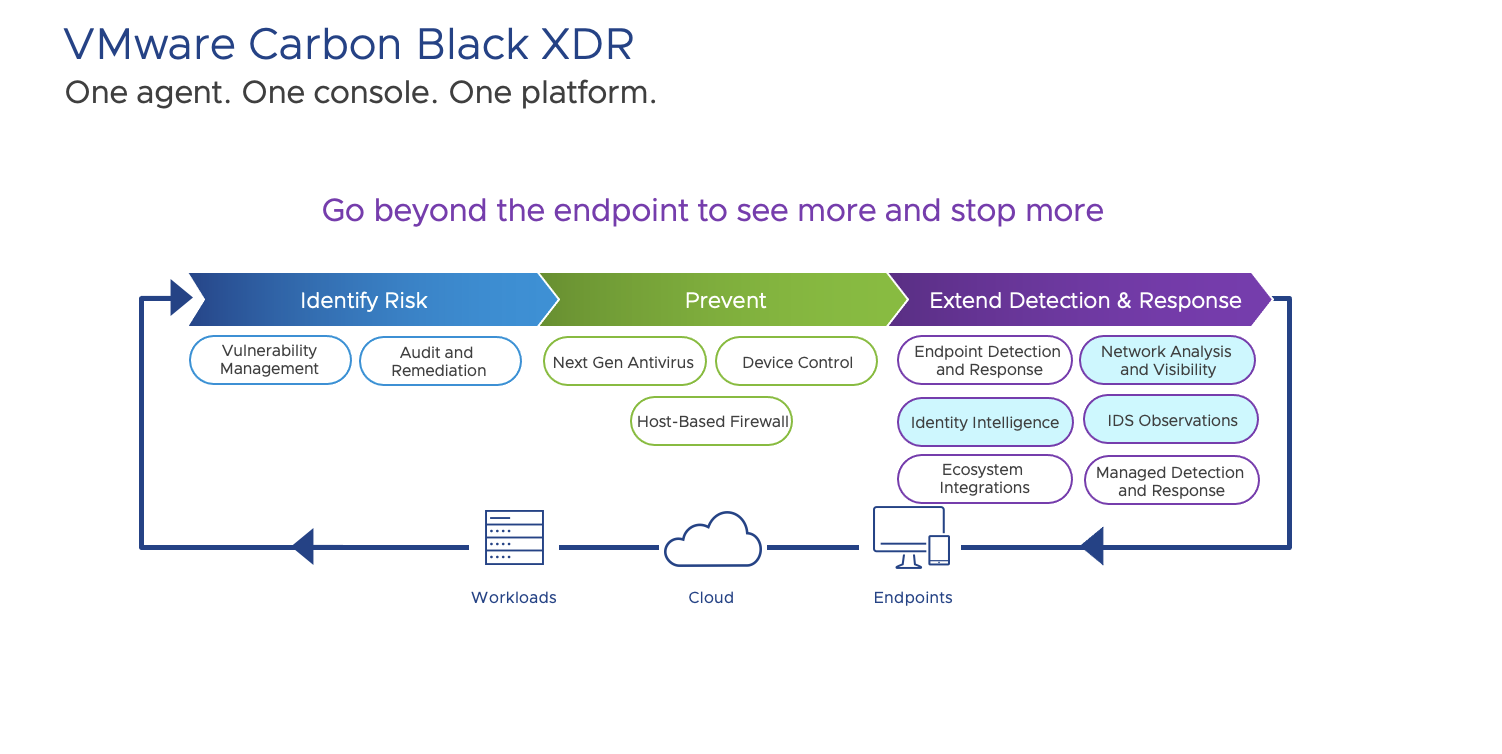
VMware Carbon Black XDR goes beyond the endpoint to see more and stop more.

How does it work?
VMware Carbon Black XDR adds Identity Intelligence, Intrusion detection and network visibility to the Carbon Black Cloud (CBC), strengthening lateral security and overall visibility. This XDR telemetry deploys with no changes to infrastructure.

Identity Intelligence has been added to the CBC, providing visibility to user-centric events that are indicative of malicious activity and correlates this user data with process and network connection visibility.
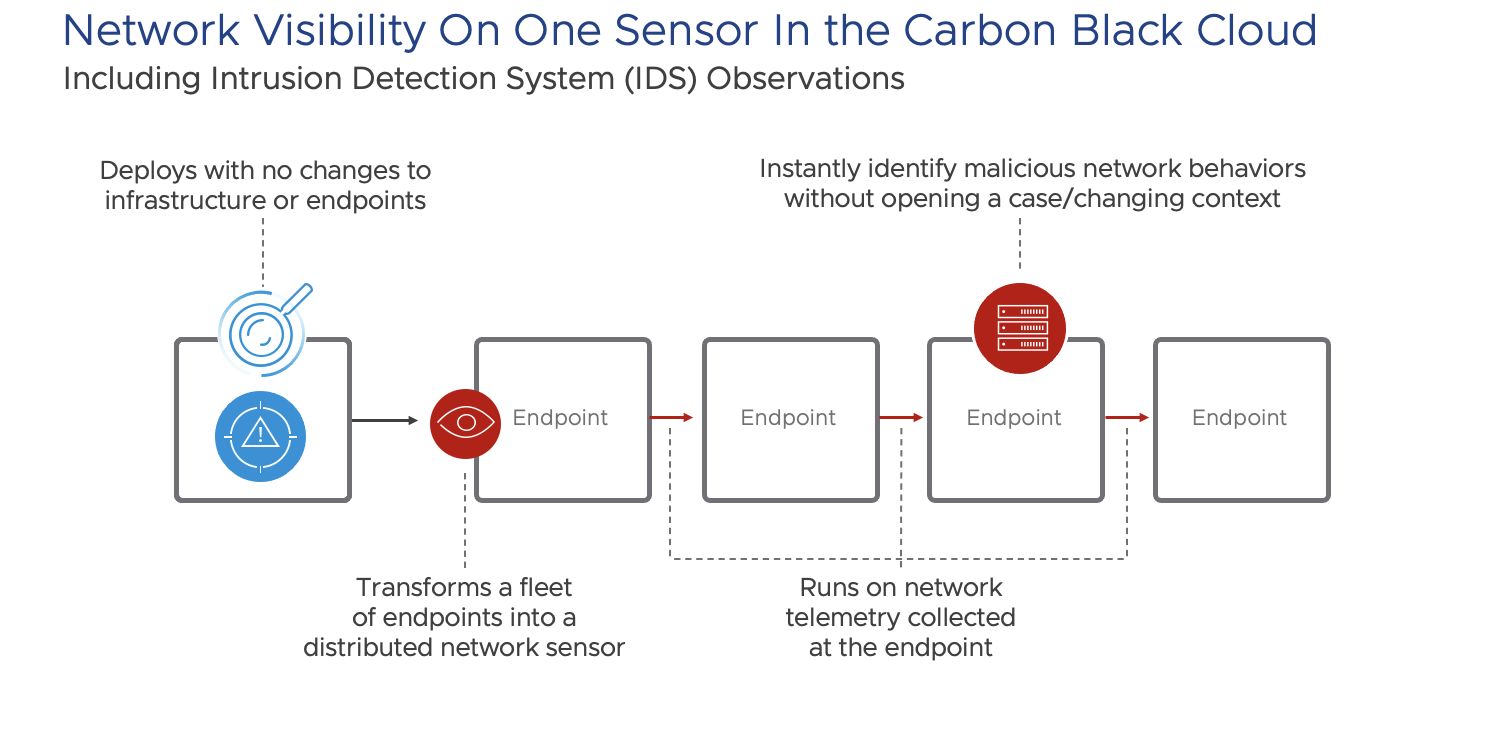
The network sensor is integrated with our existing Carbon Black Cloud sensor, therefore there is no need for network taps or to deploy additional software. No changes to the network config or networking are required to get the additional visibility. We now have NDR data and telemetry in the CBC console. This new telemetry is fully searchable, and we can create custom IOCs based upon this new data. We transform your endpoints and workloads into a fleet of distributed network sensors.
What is the difference between Carbon Black XDR and Carbon Black EDR?
EDR refers to a security solution that detects and responds to threats on endpoints, such as desktops, laptops, and workloads. Carbon Black Enterprise EDR achieves this by continuously recording and storing endpoint activity data (processes and binaries), allowing security professionals to hunt threats for abnormal activity using threat intelligence and customizable detections in real time and visualize the complete attack kill chain.
XDR, on the other hand, is a more comprehensive security solution that goes beyond endpoints and integrates data from multiple control points.
By extending Carbon Black Enterprise EDR, Carbon Black XDR delivers on modernizing the SOC by enabling rapid and accurate detection, visualization and analysis of endpoint, network, workload, and user data in context.
Carbon Black XDR surfaces new results by preserving and extending the endpoint and network contexts during analysis and display.
In addition to the Identity Intelligence, interactive and expandable attack chain visualization and out of the box customizable behavior detection you get with Carbon Black Enterprise EDR, we add IDS, network visibility and XDT tagging.
Carbon Black XDR:
- Transforms a fleet of endpoints into a distributed network sensor
- Delivers pervasive visibility across endpoints, workloads, networks, and users in an open scalable ecosystem
- Reduces blind spots that leave attackers nowhere to hide.
What are the Key Benefits of Carbon Black XDR?
Carbon Black XDR offers a significant improvement on telemetry visibility from a single pane of glass, combining the SOC and NOC and providing the complete visibility required to get the highest confidence level in the response actions taken across the environment. Ultimately reducing Mean Time To Detection (MTTD) and Mean Time To Response (MTTR).
Deploy with no changes to infrastructure.
VMware Carbon Black XDR delivers extended detection and response (XDR) telemetry deploys with no changes to infrastructure or endpoints. All that is required is the correct licensing and deploying the 3.9.x+ sensor.
Instant Visibility into Endpoints, Workloads, Network and Users
We have a purposeful built cloud; collecting all process, network and user data from a single sensor, we are not relying on disparate sources like a SIEM.
Detect and respond faster with Carbon Black XDR
Carbon Black XDR gives you the power to respond and remediate in real time, stopping active attacks and repairing damage quickly. Reducing complexity, accelerating investigations and greatly reduced dwell time and ultimately reducing Mean Time To Detection (MTTD) and Mean Time To Response (MTTR).
What are the Core Capabilities of Carbon Black XDR?
Carbon Black XDR offers the following core capabilities enabling it to provide instant visibility while strengthening lateral security, speeding up detection and response and reducing dwell time.
Network Connection Visibility
Network connection visibility enables customers to visualize and analyze network data in context, using the Carbon Black Cloud. The XDR network telemetry includes continuous capture and analysis of network fingerprints, flow and TLS data, and application-protocol data.
Identity intelligence
Carbon Black XDR Provides visibility to user-centric events that are indicative of malicious activity, such as various forms of account misuse, anomalous authentication behaviour, and insider threats.
Identity intelligence gives insight into activity of user account for context, correlation, and analysis. Insights such as log on, log off events, account changes, privilege escalation and how local domain accounts are being used on the network. While these activities can be benign, they can also indicate malicious behaviour.
IDS Observations
As traditional network defenses and perimeters lose visibility due to remote work SOC analysts can now utilize endpoints with Host based intrusion detection system (IDS) to close the gaps. IDS alerts instantly identify malicious network behaviors without opening a case or changing context.
The purpose of IDS is to detect and respond to malicious activity. We are monitoring the activity on a host for signs of suspicious behaviour, unauthorized access attempts, or unusual network traffic. We use a mix of signature-based detection and behavioural analysis to identify potential security threats.
XDR TTP tagging
Analysts benefit from Carbon Black Tactics Techniques Procedures (TTP) tagging, where the mapping to TTP within the MITRE ATT&CK framework is automatic. Carbon Black XDR adds TTP tags to network visibility events as well.
New Observations UI
Observations are “items of interest,” events which do not merit alert-level action but may be useful as “indicators” for hunting or additional investigation. Observations are the noteworthy, searchable findings across your whole fleet and lets you see interesting or suspicious activity in your environment that does not always reach the importance of generating an alert.
Attack Chain Visualization & Search
Enterprise EDR provides intuitive attack chain visualization to make identifying root causes fast and easy. Analysts can quickly jump through each stage of an attack to gain insight into the attacker’s behaviour, close security gaps, and learn from every new attack technique to avoid falling victim to the same attack twice.
Carbon Black XDR extends this visualization by delivering network visibility within the same console. The analyst doesn't need to switch contexts or open a case with the network team. We are enabling customers to visualize and analyse network data in context, using the Carbon Black Cloud.
Open Ecosystem XDR
Carbon Black boasts a robust partner ecosystem and open platform that allows security teams to integrate the Carbon Black Cloud into their existing security stack.
Flexible Platform
Carbon Black XDR is available on our Carbon Black Cloud platform making XDR scalable, flexible and easy to use while reducing costs and improving security and collaboration between the SOC and NOC.
Top 5 Things you should know about Carbon Black XDR?
Where does Carbon Black XDR Ingest data from?
With Carbon Black XDR, you can gain unified visibility with one agent, one console, one platform.
Customers can go beyond the endpoint to see and stop more.
Carbon Black XDR offers a significant improvement on telemetry visibility from a single pane of glass, combining the SOC and NOC and providing the complete visibility required to get the highest confidence level in the response actions taken across the environment. The Identity and network sensor is integrated with our existing Carbon Black Cloud sensor, therefore there is no need for network taps or to deploy additional software. No changes to the network config or networking are required to get the additional visibility. We transform your endpoints and workloads into a fleet of distributed network sensors.
Why choose Open Ecosystem XDR?
Open ecosystem XDR approaches harness the best visibility data possible from a variety of systems, connecting across control points and facilitating security automation. Open XDR is vendor agnostic and flexible it allows for best-of-breed security, leverage existing tools with no need to rip and replace.
This “open” approach contrasts with closed or SIEM-only approaches. Closed ecosystem XDR forces teams to rip-and-replace existing infrastructure and become locked into a single vendor, meaning that security teams are not able to leverage best-of-breed products.
VMware Carbon Black XDR participates in open ecosystem XDR through the XDR Alliance (https://www.xdralliance.com/), a group of best-in-class security and information technology providers organized to help security teams easily design and implement effective threat detection, investigation, and response capabilities.
What is an Observation?
The Observations page lets you see interesting or suspicious activity in your environment that does not always reach the importance of generating an alert. This page lets you search through the stream of notable activities on one or more devices; you can avoid researching all the raw events that are reported by every asset. This page provides a convenient means by which to perform a sweeping search across all your organization's assets. Observations are the noteworthy, searchable findings across your whole fleet. They complement raw events on Process Analysis page.
We provide observations from all our engines, including our new IDS engine. For a full list please refer to the Carbon Black Cloud User Guide.
Does Carbon Black map XDR data with the MITRE ATT&CK Framework?
MITRE ATT&CK Tactics & Techniques MITRE ATT&CK® is visible throughout the Carbon Black Cloud console as well as in XDR.
MITRE ATT&CK is widely adopted by the security industry as a knowledge base of adversarial tactics and techniques. For more information about MITRE ATT&CK, see MITRE ATT&CK (external link).
A Tactic represents the purpose behind a technique. For example, a MITRE ATT&CK Tactic ID of TA0001 signifies that the adversary is trying to penetrate your network.
A Technique expresses how the adversary is attacking. For example, a MITRE ATT&CK Technique ID of T1548.003 indicates that adversaries are performing sudo caching to elevate privileges.
You can filter and search on Tactic and Technique fields on the Observations, Alerts, Processes, and Process Analysis pages. You can sort on these fields as well.
Is there a hands-on demo available?
Yes there is. Please use the TestDrive experience, which enables you to run a live attack and then investigate what the attack did using Carbon Black XDR.
Summary and Additional Resources
Conclusion
This document provides you with a good understanding and overview of the Carbon Black XDR architecture. To learn more about the product, please refer to our TestDrive experience.
Additional Resources
For more information about Carbon Black XDR, explore the Mastering XDR activity path. The activity path provides step-by-step guidance to help you increase your understanding of Carbon Black XDR, including articles, videos, and labs. We also have the following areas for additional documentation and support:
- VMware Docs – Product documentation, OER guides.
- Uex – Carbon Black User exchange and community pages
- Developer Network – Details on our Open APIs, integrations, and platform SDKs.
Changelog
The following updates were made to this guide:
|
Date |
Description of Changes |
|
2023/03/06 |
|
Feedback
Your feedback is valuable.
To comment on this paper, contact VMware Security Business Unit Technical Marketing at sbu_tech_content_feedback@vmware.com.
Authors and Contributors
With significant contributions from:
- Raj Sahota, Senior Tech Marketing Architect, Carbon Black
