Carbon Black Cloud Workload User Guide for vSphere admins
Carbon Black Cloud Workload Overview
VMware Carbon Black Cloud Workload Protection provides vulnerability assessment and inventory management for workloads hosted on vSphere. The VMware Carbon Black Cloud Workload Protection vulnerability solution provides shared information on vulnerabilities that is available in Carbon Black Cloud as well as in the native vCenter administration client.
Prevention and threat hunting capabilities can be extended beyond vSphere workloads to your endpoints (desktops, laptops, servers, VMs, etc.).
This document provides the vSphere administrator with a foundational body of knowledge concerning the Carbon Black Cloud Workload Plug-in and how it is utilized in the overall Carbon Black Cloud Workload Protection architecture.
Section 1: Introduction to Cloud Workload Protection
VMware Carbon Black Cloud Workload Protection provides vulnerability assessment and inventory management for workloads hosted on vSphere. The VMware Carbon Black Cloud Workload Protection vulnerability solution provides shared information on vulnerabilities that is available in Carbon Black Cloud as well as in the native vCenter administration client. Workload protection capabilities are fully integrated into the world’s leading cloud management platform for complete data center visibility and protection. The solution combines vSphere and VMware Carbon Black Cloud in a purpose-built, operationally simple solution with minimal overhead and performance impact.
VMware Carbon Black Cloud Workload Protection solution is the only vSphere vCenter workload protection platform for enterprise virtualization and security teams that delivers the most secure virtual infrastructure, while also providing the same visibility and capabilities within the public cloud as well.
The Carbon Black Cloud Workload Protection solution reduces the attack surface by giving Infrastructure, DevOps, and Security teams visibility into the operating system and application vulnerabilities right from within the vCenter Management plane as well as within the Carbon Black Cloud Management Console.
Cloud Workload Protection Architecture
A Carbon Black plug-in within vCenter allows for a shared truth on vulnerabilities and risk for those residing in vSphere/infrastructure as well as team members more focused on security or the Carbon Black Cloud console. Through this unique approach, we can eliminate the trade-off between security and operational simplicity by providing a single source of truth for Infrastructure and Security teams to accelerate response to critical vulnerabilities and attacks, while enabling collaboration and reducing friction. The Carbon Black Cloud Workload Plug-in provides deep visibility into your data center inventory and end-to-end life-cycle management for the components.
VMware Carbon Black Cloud Workload Protection contains two Carbon Black Cloud Workload Protection components:
- Carbon Black Cloud Workload Protection Plug-in in vCenter
- Carbon Black Cloud Management Console
For further information on the solution architecture reference the following resource: https://carbonblack.vmware.com/resource/carbon-black-cloud-workload-protection-architecture
Installation Walkthrough
For purposes of this user guide, CWP is assumed to already be installed and configured. For information on installing and configuring CWP in under 15 minutes see the following video: https://youtu.be/M_SZXsqCYOY
For a detailed step by step guide to installing the Carbon Black Cloud Workload Appliance, please see the document, Carbon Black Cloud Workload Appliance Checklist and Quick Install Guide.
Section 2: Walkthrough of vSphere with the Carbon Black Cloud Workload Plug-in
The following section details the basics of accessing and using the Carbon Black Cloud Workload Plug-In in vSphere. The Carbon Black Cloud Workload Plug-in for vSphere integrates Carbon Black security capabilities directly in the vSphere Client.
vCenter Cloud Workload Protection (CWP) Plug-in
Once logged in, to view the Carbon Black Cloud Workload Plug-in, click Menu at the top to expose menu options. Then select the Carbon Black icon in the drop-down menu. The plug-in can also be accessed on the left-hand side of the vSphere console.
Note: If you receive the error "Unable to fetch appliance details, please contact the administrator", hit the browser refresh button.
Cloud Workload Protection Plug-in Navigation
Summary Tab
On accessing the plug-in, you will be brought to the Summary, or "Dashboard", tab. The Carbon Black Cloud Workload Plug-in Summary tab contains widgets on appliance health, inventory status, and critical vulnerabilities:
Appliance Health: The CWP appliance facilitates communication between your vSphere environment and the CBC. Appliance Health displays the status of the CWP appliance. For more information on appliance status see the following page: https://docs.vmware.com/en/VMware-Carbon-Black-Cloud-Workload/1.0/carbonblack_workload/GUID-66E2A35A-4754-43F6-A5AD-C611D35EDD44.html
- Inventory Status: Inventory management for workloads; shows the coverage of Carbon Black through vSphere environment (is Carbon Black enabled, if there are updates to Carbon Black sensor available, are assets eligible for Carbon Black, assets unsupported by Carbon Black, etc.)
- Affected Assets: Displays how many assets are affected by vulnerabilities, broken down by OS
- Critical Product Vulnerabilities: Displays how many critical vulnerabilities are present in the environment by vulnerability type (Windows OS, Windows App, Linux OS, Linux App)

Vulnerabilities Tab
The Vulnerabilities page displays vulnerabilities present in your vSphere environment. Click "Vulnerabilities" to navigate the vulnerability page.
An overview of vulnerabilities is shown at the top of the page - including filters based on vulnerability severity. Severity scoring allows for administrators to understand and mitigate risks in a prioritized, realistic method. Higher severity scores indicate that the vulnerability should be prioritized. There are four severity categories…
- Low: Score from 0.0 – 3.9
- Moderate: Score from 4.0 – 6.9
- Important: Score from 7.0 – 8.9
- Critical: Score from 9.0 – 10.0

As a vCenter Server administrator, you want to have visibility of known vulnerabilities in your environment to understand your security posture and schedule maintenance windows for patching and remediation. With the help of vulnerability assessment, you can proactively minimize the risk in your environment.
Vulnerabilities can be viewed in Asset View or Vulnerability View:
- Asset View displays workloads covered by CWP and allows you to look at all vulnerabilities affecting the workload of interest.
- Vulnerability View displays all vulnerabilities based on type (Windows OS, Windows App, etc.).
Carbon Black investigates vulnerabilities related to:
- Operating System (OS) of the virtual machine.
- Windows OS: Displays OS-level vulnerabilities for Windows VMs. The system looks for OS details and the security patches applied on each VM. When the security patch associated with the vulnerability is not applied, the VM is flagged as vulnerable.
- Linux OS: Displays OS-level vulnerabilities for Linux VMs. The system looks for OS details with the list of all installed packages. The system determines the vulnerable packages installed on the VM and reports the CVEs against those packages.
- Applications are installed on the virtual machine.
- Windows Apps: Displays application-level vulnerabilities for the Windows VMs.
- Linux Apps: Displays application-level vulnerabilities for the Linux VMs.

Inventory Tab
The Inventory page displays workloads for which you have enabled and not enabled CWP. You can manage workloads from this page.
CWP provides a streamlined sensor deployment process. The Carbon Black sensor installer is provided as part of the VMware Tools package. Deployment to workloads is simplified to a ‘click to enable’ process. Simply select the workload for which you would like to enable CWP and click ‘Enable’. Initial assessment begins within 24 hours of enabling, and then occurs daily, automatically from that point forward.

Major sensor updates can be pushed by selecting workload(s) and clicking the ‘Update’ button. Only major sensor updates need to be manually done from the vCenter plugin or Carbon Black Cloud console. Updates can be done individually or on multiple/all workloads.
How Carbon Black Measures Risk
Carbon Black Cloud partners with Kenna Security to leverage the largest database of vulnerability, exploit, and event threat data in the industry. This data is distilled into three main measures of risk:
- Active Internet Breach: Presence of near-real-time exploitation.
- Malware Exploitable: Availability of an exploit module in a weaponized exploit kit.
- Easily Exploitable: Availability of a recorded exploit.
There are metrics defined for Common Vulnerability Scoring System (CVSS). A few of the metrics are about the attack method itself, whereas the others depend on how the application assesses impact - the direct consequence of a successful exploit. To learn more about CVSS, visit https://www.first.org/cvss/specification-document.
Risk Score
Every vulnerability is assigned a risk score of between 0.0 (no risk) and 10.0 (maximum risk). The risk score range and severity are defined as follows.
|
Score Range |
Severity |
|
0.0–3.9 |
Low |
|
4.0–6.9 |
Moderate |
|
7.0–8.9 |
Important |
|
9.0–10.0 |
Critical |
To learn more about how the risk is calculated, refer to the Kenna Security documentation available at https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/docs/vmwcb-whitepaper-understanding-the-kenna-security-vulnerability-risk-score.pdf.
Section 3: Identifying Risks with vCenter Carbon Black Cloud Workload Plug-in
VMware Carbon Black Cloud Workload Protection consolidates multiple datacenter security capabilities with an easy deployment experience on vSphere and a single lightweight sensor used throughout your workload environment. VMware Tools includes the Carbon Black sensor installer, facilitating the installation process and eliminating management by providing native security capabilities as a service that IT infrastructure owners can provide.
Workload protection allows us to discover and view any risks that have been identified by our vulnerability assessment capability. With this capability there is no scanning involved because we are already collecting the data, we are leveraging the same single data stream to query and populate this data within the vCenter management plane.
Looking into a Critical Vulnerability
While logged into vCenter, click on the Menu button at the top of vCenter and then navigate to and click on the Carbon Black plug-in. For more information on accessing and navigating the plug-in see section 2.2.
Navigate to the Vulnerabilities page within the plugin. The Vulnerabilities page displays information on vulnerabilities affecting the environment with intuitive filtering capabilities to give administrators a prioritized, realistic method to look at risk and threat.
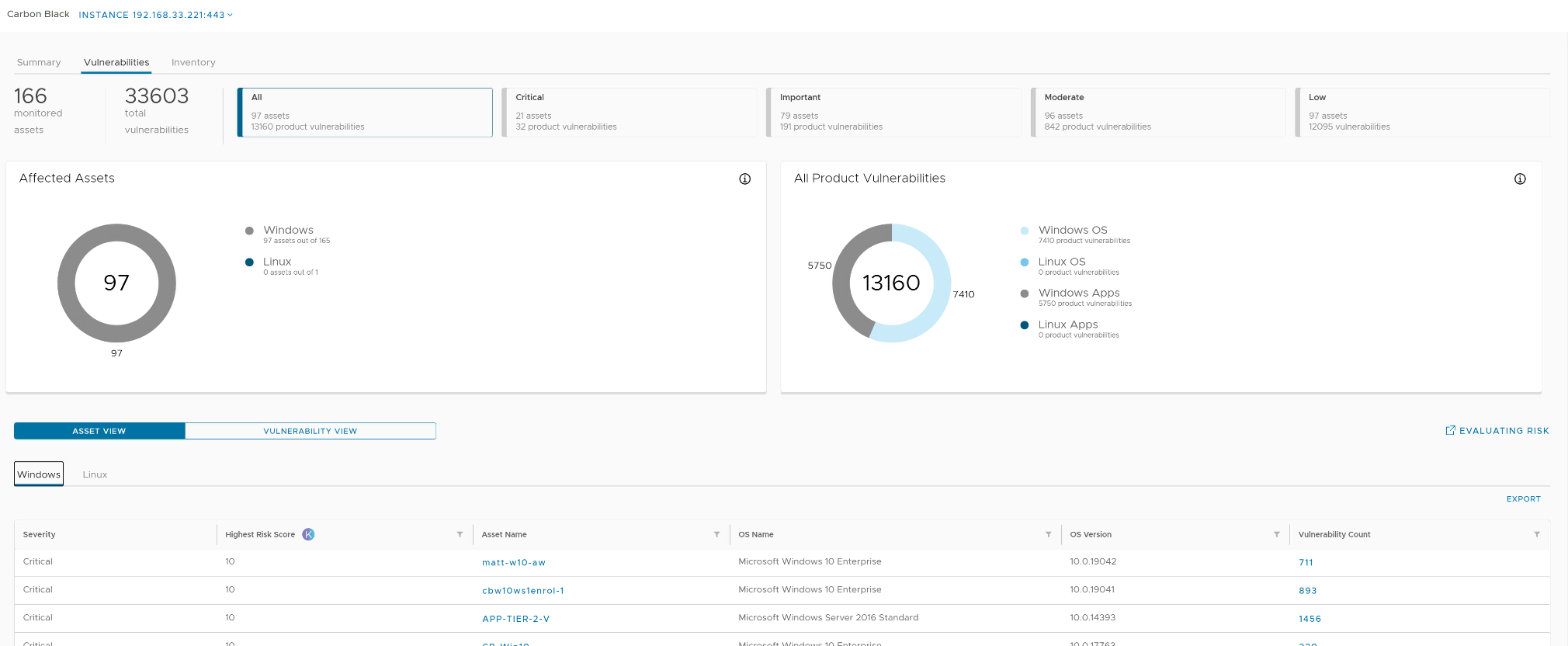
On the top of the page severity level filters can be used to view vulnerabilities in a prioritized manner. We will focus on Critical vulnerabilities, with a severity score of 9.0 to 10.0. For more information on how risk is scored see Section 2.3.
- If not currently selected, click the Critical filter at the top of the page to view only critical vulnerabilities

We should now see only Critical High-Risk score CVE’s, these are CVE’s that are exploitable within this environment. This means an attacker (external or internal) could gain access to a workload by leveraging one of these CVEs in an attack if discovered.
- Scroll down to view vulnerabilities
- Click the Vulnerability View to view all vulnerabilities based on the type

Vulnerability types include Windows OS, Linux OS, Windows App, and Linux App. Select a vulnerability type of interest.
A vulnerability will display:
- Severity: Criticality of a vulnerability
- Risk Score: Score denoting severity; ranges from 0.0 (no risk) to 10.0 (maximum risk)
- OS Name: Name of OS affected by the vulnerability
- OS Version: Version of OS affected by the vulnerability
- CVE ID: Identifier of the specific vulnerability
- Fixed by: If applicable, links to KB article denoting update/patch that fixes a vulnerability
- Vendor (if App vulnerability): Name of the vendor of application w/vulnerability
- Product Name (if App vulnerability): Name of application w/vulnerability for reference
- Version (if App vulnerability): Version of App vulnerability is fixed by
- Assets Affected: Number of workloads in your environment that are affected by this vulnerability
- Click the carrot next to a vulnerability to expand additional information

Expanding a vulnerability will show:
- A plaintext description of the vulnerability
- Link to the National Vulnerability Database
- Asset(s) affected by the vulnerability
- Risk details (Kenna variables affecting severity score)
- CVSS score information
- CVSS vector details
- Click the link to the National Vulnerability Database

CWP directly links to the National Vulnerability Database (NVD) page for the selected vulnerability. This allows for an easy workflow to get more background on the vulnerability and how to resolve it directly in your vSphere environment.
- Review information on NVD
- Click the vSphere tab to return to the CWP plug-in
- Click the plus to expand Affected Assets
- Click one of the Affected Assets

When viewing a workload, on the Monitor tab, a Carbon Black Vulnerabilities page is available. You can view all vulnerabilities affecting a particular workload from this page.

We have now completed a workflow looking into a critical vulnerability directly in vSphere. CWP provides built-in vulnerability assessment capabilities in your vSphere console.
Summary and Additional Resources
This user guide covers the VMware Carbon Black Cloud Workload Protection solution using the vCenter plug-in.
Additional Resources
Contact
Carbon Black Workload Protection
- TechZone Mastering Carbon Black Workload: https://carbonblack.vmware.com/mastering-carbon-black-workload
- TechZone Installing Carbon Black Workload Appliance in Under 15 Minutes: https://via.vmw.com/tchz24b2b1d7no3036
- TechZone vSphere Admin Best Practice Guide for Carbon Black Cloud: https://via.vmw.com/tchz24b2b1d7no3082
- Workload Protection Hands-on Lab: https://labs.hol.vmware.com/HOL/catalogs/lab/10212
Carbon Black TestDrive Experiences
- Malware Lab (Endpoint Protection): https://kb.vmtestdrive.com/hc/en-us/articles/4404323100187-VMware-Carbon-Black-Cloud-Malware-Lab
- Container Security: https://kb.vmtestdrive.com/hc/en-us/articles/1260803985870-Securing-Modern-Applications-with-CBC-Container-Security
Changelog
The following updates were made to this guide.
|
Date |
Description of Changes |
|
2022-02 |
Initial publication |
About the Author and Contributors
Dale McKay is a technology evangelist and strategist with deep expertise in security, virtualization, and networking. He has extensive knowledge of a variety of technologies for meeting the strategic and tactical needs of clients. He has strong real-world, hands-on skills in cybersecurity, with his focus being on implementing policies and operating procedures that help his customers address their cybersecurity demands. He is an experienced leader in determining client needs, delivering solutions, and building relationships.
Dale McKay, Senior Technical Marketing Architect, Network and Advanced Security Business Group, VMware
