Apache Commons Text Vulnerability
On October 13, 2022 the NIST National Vulnerability Database published a CVE from Apache Software Foundation known as CVE-2022-42889. This is a critical vulnerability, with NIST giving it a score of 9.8.
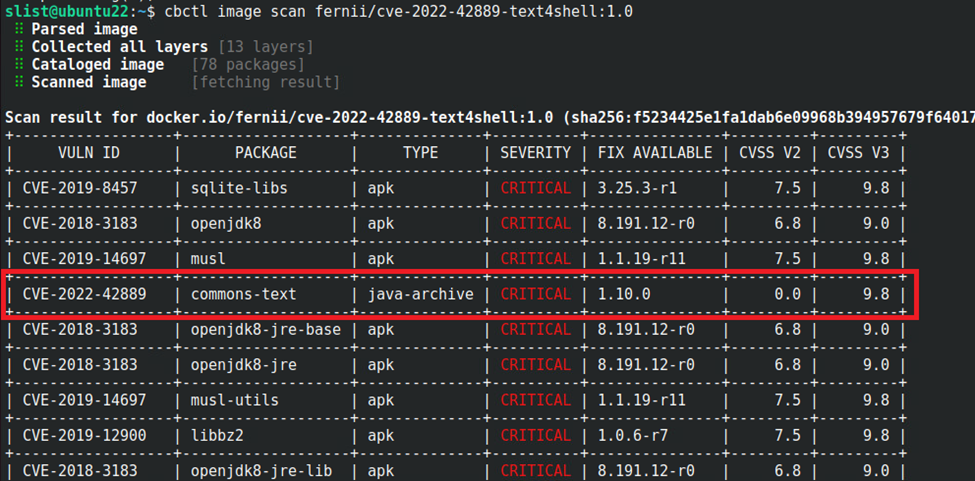
In further investigation, Apache Commons Text versions 1.5-1.9 are vulnerable, but a fix is available in version 1.10. Apache Commons Text is a Java library focused on algorithms working on strings. The file name of the library for version 1.6 is commons-text-1.6.jar, and it can be included in a container image with the name “commons-text”.
In order to be vulnerable, the Java application code must use the StringSubstitutor interpolator of the library. This vulnerability then allows remote code execution (RCE) - an attacker can access the vulnerable host and execute arbitrary code. The vulnerability is easy to use and exploits are available, but unlike log4j the vulnerable API is not widely used, and thus there are far fewer servers affected than for the earlier log4j critical vulnerability.
For VMware Carbon Black Customers
How to tell if a VMware Carbon Black customer was affected
- VMware Carbon Black Container customers can manually scan their container image in their container repository using cbctl.

- Carbon Black Container customers will automatically see if a container image running in their Kubernetes clusters is vulnerable to CVE-2022-42889 with the “runtime scanner” feature.


- Using the network runtime capabilities of Carbon Black Container, all network connections of pods running in Kubernetes are learned by Carbon Black and any deviation from the normal behavior will generate an alert if a pod connects to the malicious infrastructure of the attacker.
- Using Tanzu Service Mesh, you can create network rules to isolate or block connections from the vulnerable pods to public IPs.
How to inspect your level of exposure
Carbon Black Container will detail the layer of the container image with the vulnerability and will show all pods/namespaces/clusters with the vulnerability.
How to remediate the CVE or prevent exposure
As shown by the Carbon Black Container user interface, a fix is available in version 1.10 of the commons-text library.
Customer next steps
Prioritize the patching of your container images with the Carbon Black Container dashboard. A good practice tip is to patch first critical vulnerabilities with fixes.

If it’s not already done, integrate a vulnerability scanner like cbctl in your CI/CD pipeline, no matter which one you are using: Jenkins, GitLab, Tanzu Application Platform.
To read more on VMware’s response to CVE-2022-42889, check out our knowledge base article.
The CVE was published in NIST National Vulnerability Database on 10/13/2022 by Apache Software Foundation. The CVE-2022-42889 was published in National Vulnerability Database on
VMware response to the CVE: https://kb.vmware.com/s/article/8986.
The level of severity for CVS V3 score of this vulnerability is 9.8 - critical.
Impact
Apache Commons Text versions 1.5 to 1.9 are vulnerable. A fix is available in version 1.10. Apache Commons Text is a Java library, the file name of the library for version 1.6 is commons-text-1.6.jar, and it can be included in a container image with the name “commons-text”. The Java application code must use the StringSubstitutor interpolator of the library to be vulnerable.
Summary and Additional Resources
About the Author and Contributors
-
Stéphane List, Staff Technical Marketing Architect, Network and Advanced Security Business Group, VMware