A guide to VMware Cybersecurity Assessment
The Cybersecurity Assessment enables individuals and organizations to quickly assess the core cybersecurity capabilities contained in the framework to confirm strengths and identify any gaps and weaknesses.
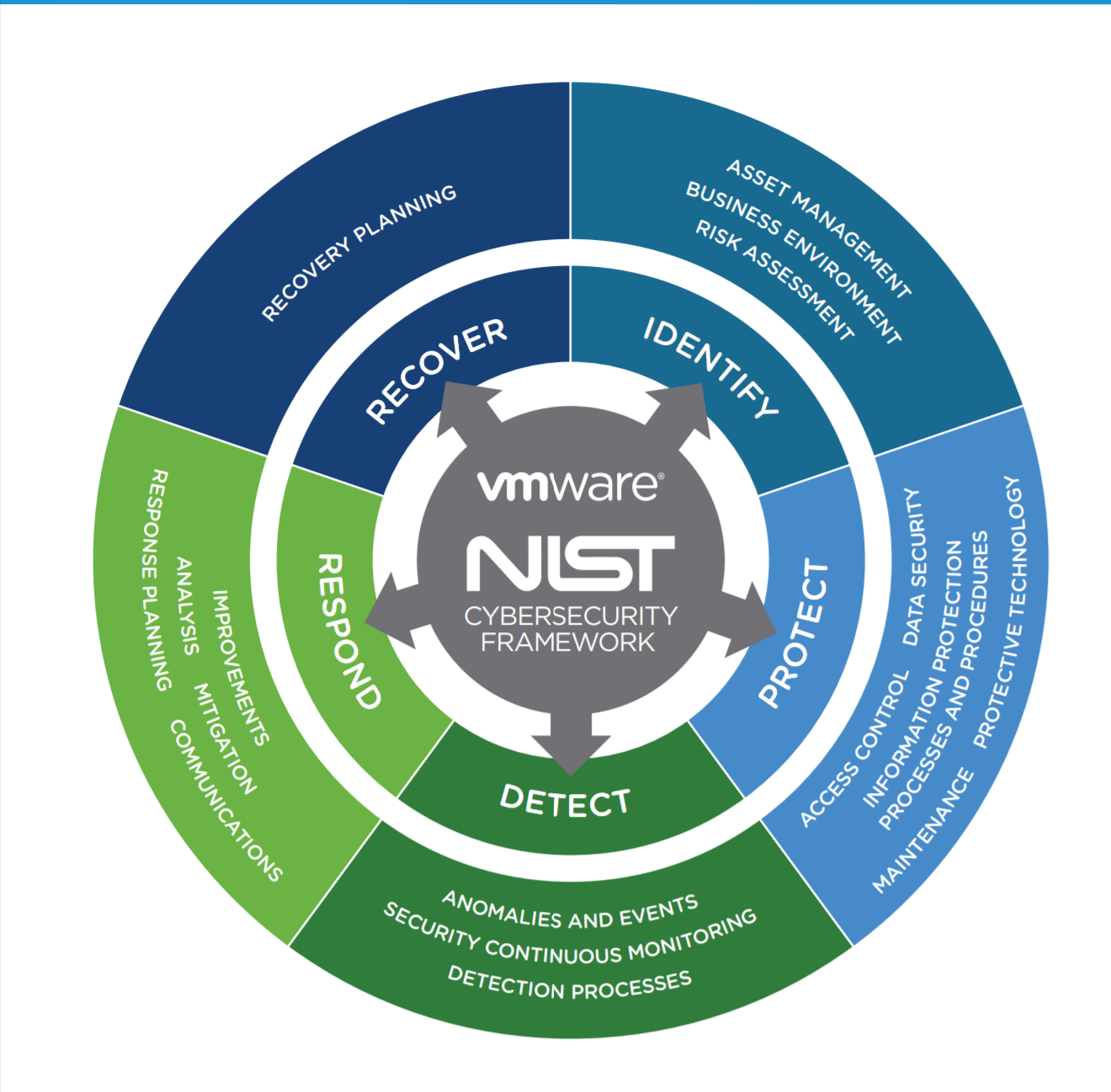
The Cybersecurity Assessment has modeled off the NIST Cybersecurity framework. The NIST (National Institute of Standards and Technology) is a physical sciences laboratory and a non-regulatory agency of the United States Department of Commerce. They created the NIST Cybersecurity framework in collaboration with industry and government and it is a voluntary framework consisting of standards, guidelines, and practices that promote the protection of critical infrastructure. The prioritized, flexible, repeatable, and cost-effective approach of the Framework helps owners and operators of critical infrastructure to manage cybersecurity-related risk.
The Cybersecurity Assessment will also generate a recommended action plan that can be immediately deployed to mitigate risk and improve performance.
The Cybersecurity Assessment is hosted on a platform called Capametrix which provides the ability to collate the anonymized responses and provide market analysis. Over the course of a few months, the Cybersecurity Assessment was hosted on the Carbon Black TechZone Website and the responses we have received have revealed the following insights.
The Scope
Various industries across the world responded to the Cybersecurity Assessment including IT, Healthcare, Education, Media and Entertainment and Telecommunications (Fig. 1). Responses originated from countries such as the United States, Belgium, United Kingdom and Germany (Fig. 2). The estimated size of organization varied as well, from small organizations to large enterprises (Fig. 3)
Figure 1: Responses By Industry


Figure 3: Responses by size of Organization

Capability Maturity Levels
The Capability Maturity levels in the Cybersecurity Assessment are measured using the Capability Maturity Model (CMM). This model was originally developed as a tool for objectively assessing the ability of government contractors' processes to implement a contracted software project. The model is based on the process maturity framework first described in IEEE Software. For consistency, the Capability Maturity Model used within the Cybersecurity Assessment has been adapted around a security context.
Overall, the responses on the Cybersecurity Assessment revealed the following spectrum of maturity levels:

As a reference, the star ratings are associated with the following descriptions:
- 5 Stars - Optimized: Procedures are continuously improved through continuous monitoring and automation.
- 4 Stars - Managed: Security metrics are established to monitor the effectiveness of the procedures.
- 3 Stars - Defined: Security principles are formally defined and documented in procedures. Procedures are communicated to applicable parties and enforced.
- 2 Stars - Repeatable: Basic security principles are established and repeated processes, however, these, processes have not been formally defined.
- 1 Star - Initial: Processes are disorganized or even non-existent. Processes are mostly reactive to the environments and are not likely to be repeatable in nature.
Capability Performance
The top area of weakness that was identified overall was "Protective Technology", followed by "Anomalies and Events". These are capabilities identified within the NIST Cybersecurity Framework that fall part of the capability groups: Identify (ID), Protect (PR), Detect (DE), Respond (RS) and Recover (RC)

Protective Technology (PR.PT)
Technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
Anomalies and Events (DE.AE)
Anomalous activity is detected, and the potential impact of events is understood.
Risk Assessment (ID.RA)
The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals.
Security Continuous Monitoring (DE.CM)
The information system and assets are monitored to identify cybersecurity events and verify the effectiveness of protective measures.
Device Hardening (Custom)
Configurations of physical or virtual devices either on a hardware or software (OS) layer could potentially lead to the compromise of a system.
* Note: Device Hardening is a custom capability added to the assessment to cover the act of locking down configurations and that it is understood
Top Recommendations
The top recommendation that was identified was to "Deploy a robust protection solution": Each recommendation provides a set of steps or technologies that can cover the previously identified capability gaps.
Deploy robust protection solution
It is imperative to have a robust protection solution capable of stopping both known and unknown attacks, even those that leverage existing trusted applications for malicious purposes. The Carbon Black Cloud's Next Generation Anti-Virus is able to analyze attacker behavior patterns over time to detect and stop never-seen-before attacks, whether they are malware, fileless or living-off-the-land attacks.
Analyze application behaviors
To help differentiate whether or not a process is performing a legitimate, suspicious or malicious action, we need to understand the tactics, techniques, and procedures performed. The Carbon black Cloud protection solution enables an admin to calculate severity by analyzing behaviors and how processes interact with other applications
Control USB devices
Unapproved removable media devices connecting to the network are one attack vector that needs to be controlled in order to harden the environment's security posture. With Carbon Black Cloud you can gain visibility and control over USB devices detected in your environment. In addition, you can review USB devices, create approvals for trusted devices, and manage approvals. Approvals are global and blocking is enabled by the policy.
Apply protection policies to endpoints and workloads
With the Carbon Black Cloud protection policies, admins are able to block according to behavior (operation attempts), further than just signature-based reputation
Ensure visibility into endpoints and workloads
You can't protect what you don't see, gaining visibility into all events happening on the machine, provides contextual information on what is happening on the machine. This provides information on what processes and applications and doing and enables the discovery of anomalous behavior. Carbon Black Cloud's behavioral and enterprise endpoint detection and response system provide extensive visibility into all events happening on devices.
Take your Cyber Assessment Today!
Want to take a deeper dive into assessing your Cybersecurity posture? There is a cybersecurity assessment based on the NIST Cybersecurity Framework available here: NIST Cybersecurity Assessment
Interested in Ransomware best practices? Here is an assessment based on the CISA ransomware best practices guide: Ransomware Best Practices Assessment
References:
- NIST Cybersecurity Framework
- Capability Maturity Model

