Did you really believe that it was safe to use WSL (Windows Subsystem Linux)?
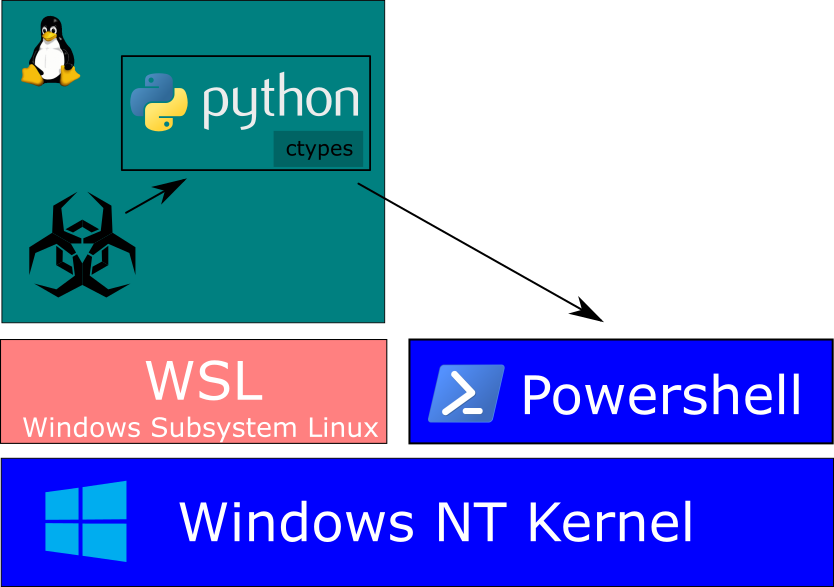
Threat researchers from Black Lotus Labs recently discovered a new attack technique.
Instead of attacking Windows directly, threat actors are able to leverage the capabilities of python running in a Linux hosted in WSL on Windows to run malicious PowerShell commands. They are using a Python library: ctypes.
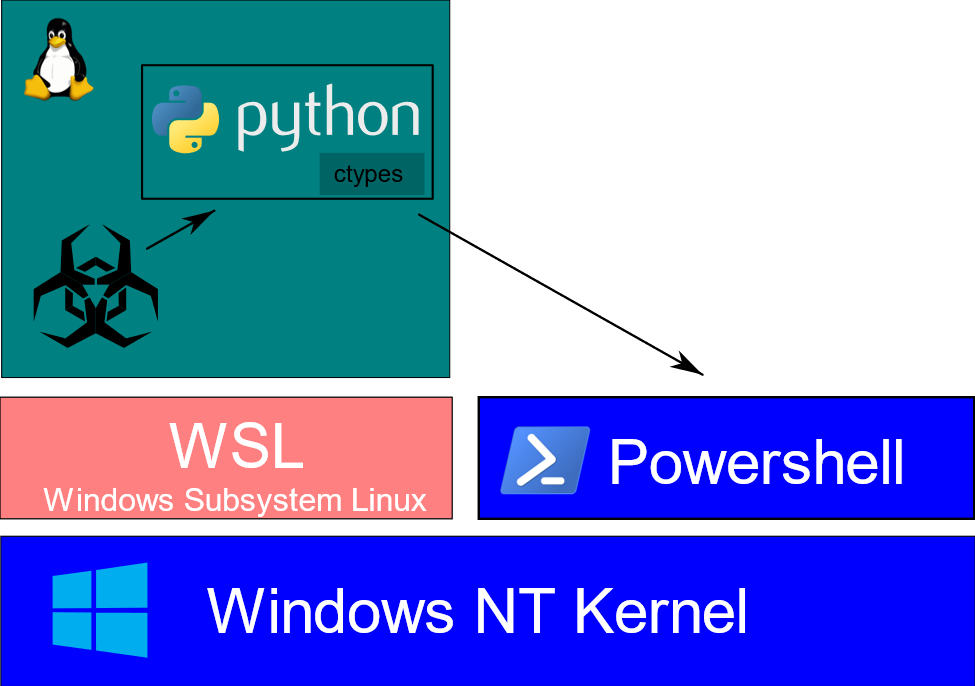
Figure1: Architecture of WSL attack
What is “ctypes”?
Ctypes is a “foreign function” library for Python, to call Windows APIs and invoke Powershell scripts. Python scripts can be converted in ELF format on Linux ( ELF: Executable and Linkable Format), so no Windows antivirus that scans Windows executables, exe, DLL... is able to scan this type of file today.
This proof of concept is uncovering just how detrimental this can be in production environments. If adversaries can access the Windows File system from the Linux subsystem, we have just opened the door to a larger attack surface than what we already know exists with standard Windows OS’s. On WSL, you can run Ubuntu, Debian… and Kali, a penetration testing distribution!
To minimize your organizational risk from my security point of view I would recommend restricting WSL access in your organization.
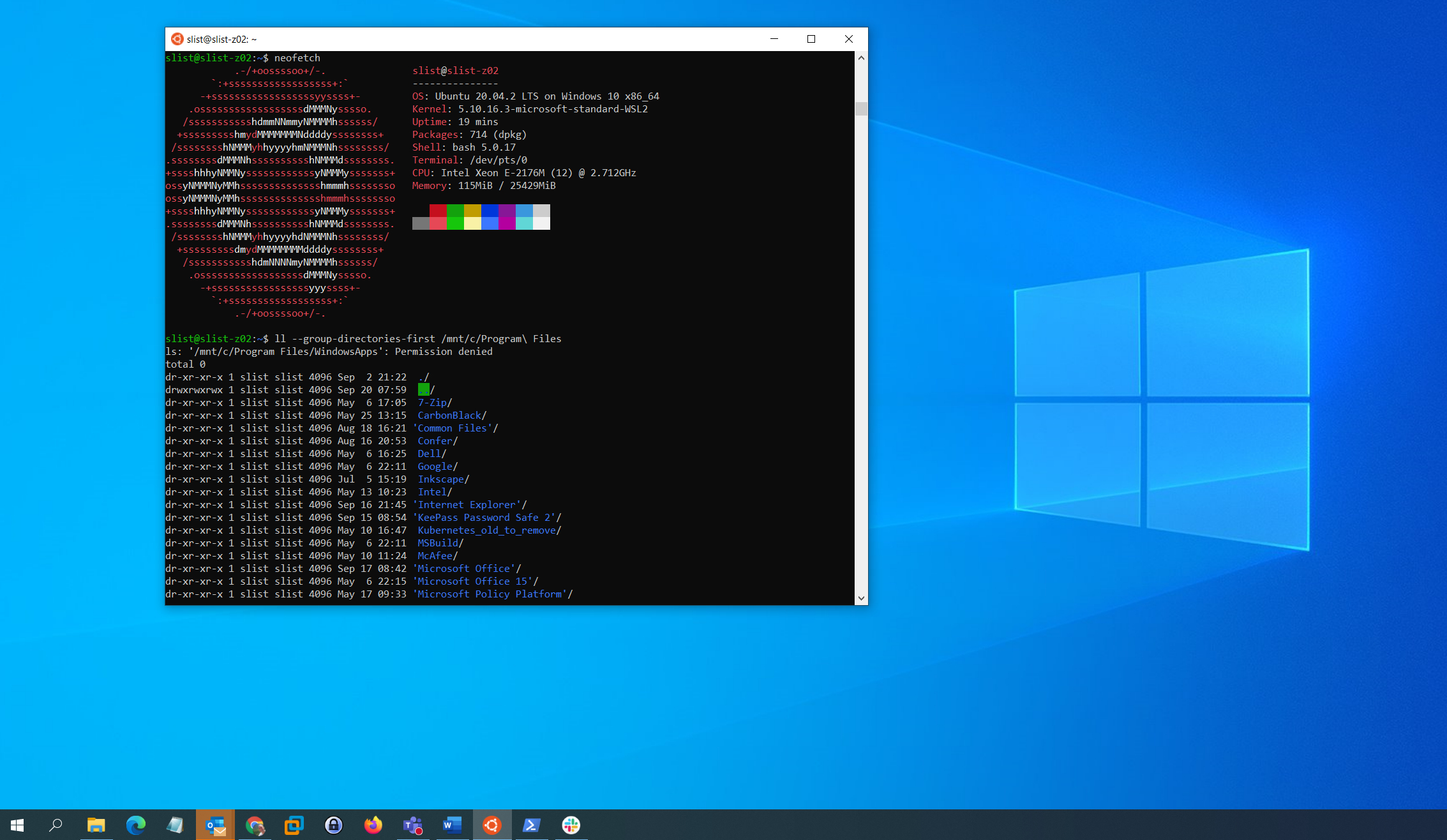
Figure2: WSL screenshot with access to Windows filesystem from Linux.
Linux Virtual Machines can be a more secure alternative to WSL; you can run Linux in VMware Workstation for example.
Verifying Usage of WSL in your Organization
So, how can you detect usage of WSL in your organization?
If you are already protecting all your Windows endpoints and workloads using VMware Carbon Black, and you have enabled the feature “Audit and Remediation” you can answer in a few seconds.
Using osquery embedded in Carbon Black Sensor, and with a web UI available in Carbon Black web UI, you can query all your endpoints using the table “windows_optional_features”:

Figure 3: osquery website, table windows_optional_features
Audit and Remediation leverage standard SQL syntax. Run the following query to identify WSL
SELECT * FROM windows_optional_features WHERE name = 'Microsoft-Windows-Subsystem-Linux' AND state = 1
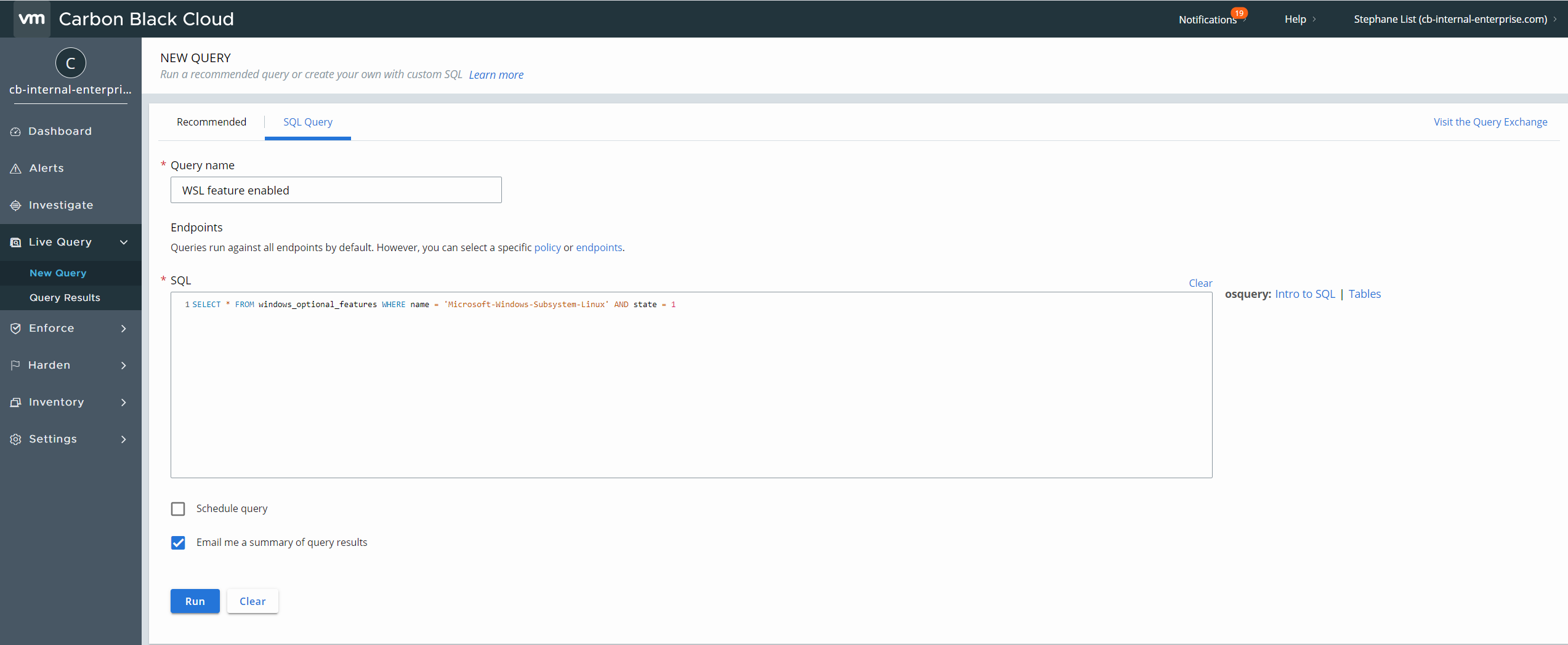
Figure 4: “Audit & Remediation” query
And a few seconds after, you will see the result:
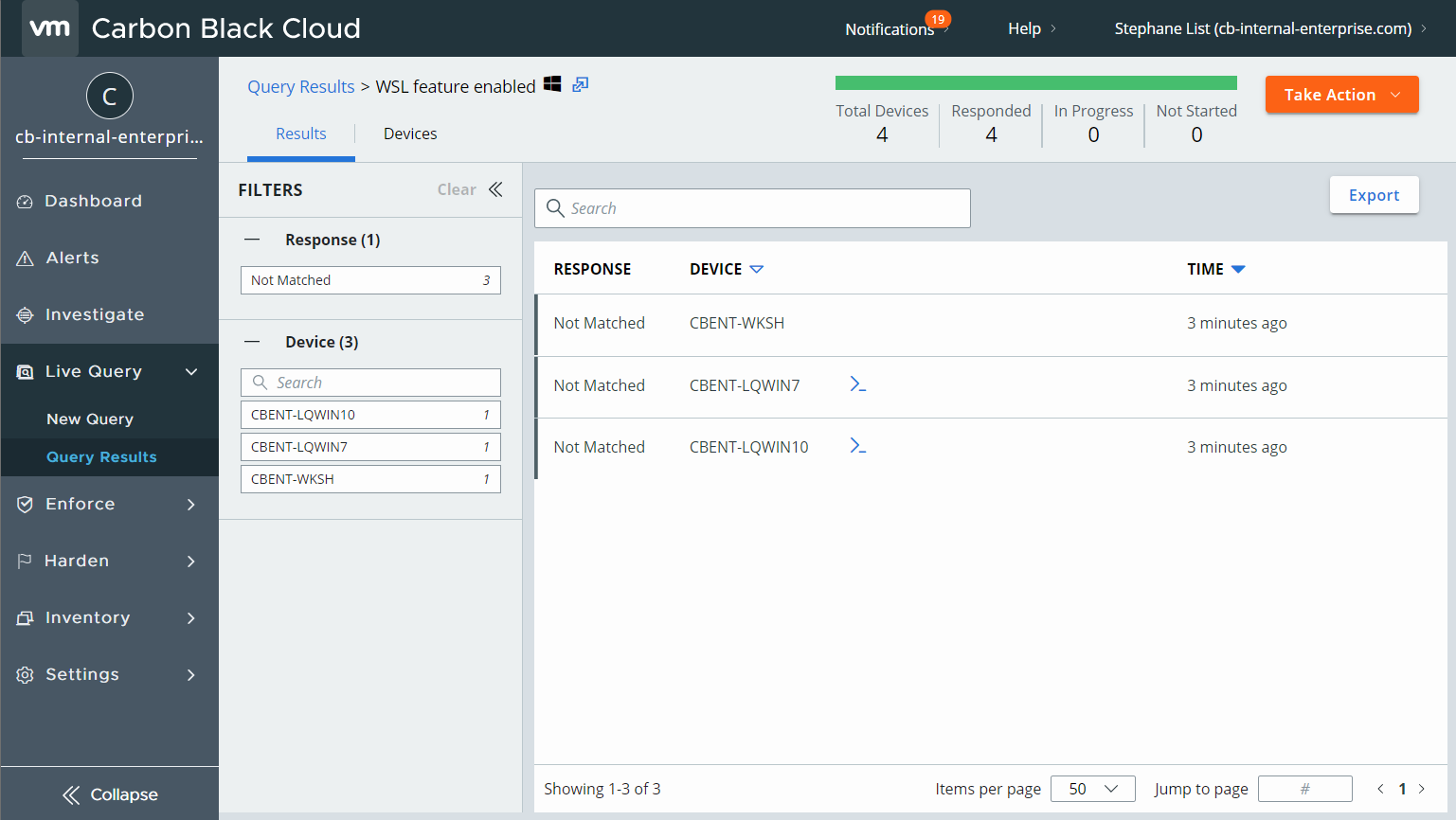
Figure 5: query result
In my test environment, there’s no WSL enabled.
I have submitted this query to our query exchange community website, and Carbon Black experts have approved and improved the query.
Conclusion
Using Linux malware running on WSL, malicious actors can take the control of your Windows endpoints. To check if your endpoints are vulnerable, you can use osquery or use VMware Carbon Black sensor that includes osquery to have all in one sensor, one console.
References:
https://docs.microsoft.com/en-us/windows/wsl/install-win10
https://osquery.io/schema/4.5.0#windows_optional_features
https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
https://community.carbonblack.com/t5/Query-Exchange/Windows-with-WSL-enabled/idi-p/107349
