Carbon Black Cloud Container Security - Technical Overview
What is Carbon Black Cloud Container Security?
VMware Carbon Black Cloud Container™ enables enterprise-grade container security at the speed of DevOps by providing continuous visibility, security and compliance for containerized applications from development to production—in any on-premises or public cloud environment. This solution provides security teams with visibility and the ability to enforce compliance while integrating seamlessly into existing DevOps processes to avoid adding operational complexity. With VMware, organizations can reduce risk, maintain compliance, and simplify security for Kubernetes environments at scale.
What are the key benefits of Carbon Black Cloud Container?

Before we take a look at the container security capabilities in depth, we can summarize the benefits we’re delivering to customers in three key areas. Similar to Carbon Black Cloud Workload, Carbon Black Cloud Container helps reducing risk by identifying vulnerabilities and misconfigurations to harden workloads.
The solution can also provide the visibility and control that devops and security teams need in order to ensure that their Kubernetes clusters and the applications deployed on them are secure and comply with all mandates and regulations in their line of business. Carbon Black Cloud Container delivers policy-based reporting and enforcement of your organization’s security posture across all workloads deployed in Kubernetes clusters, empowering you to detect and fix security risks before they become an issue. And Carbon Black Cloud Container can help customer ensure that security is maintained without slowing developers and operators down. The main goal of the container solution is to helps customer reduce their attack surface, obtain compliance, and achieve simple, secure multi and hybrid-cloud Kubernetes deployments at scale.
What are the Core Capabilities of Carbon Black Cloud Container?

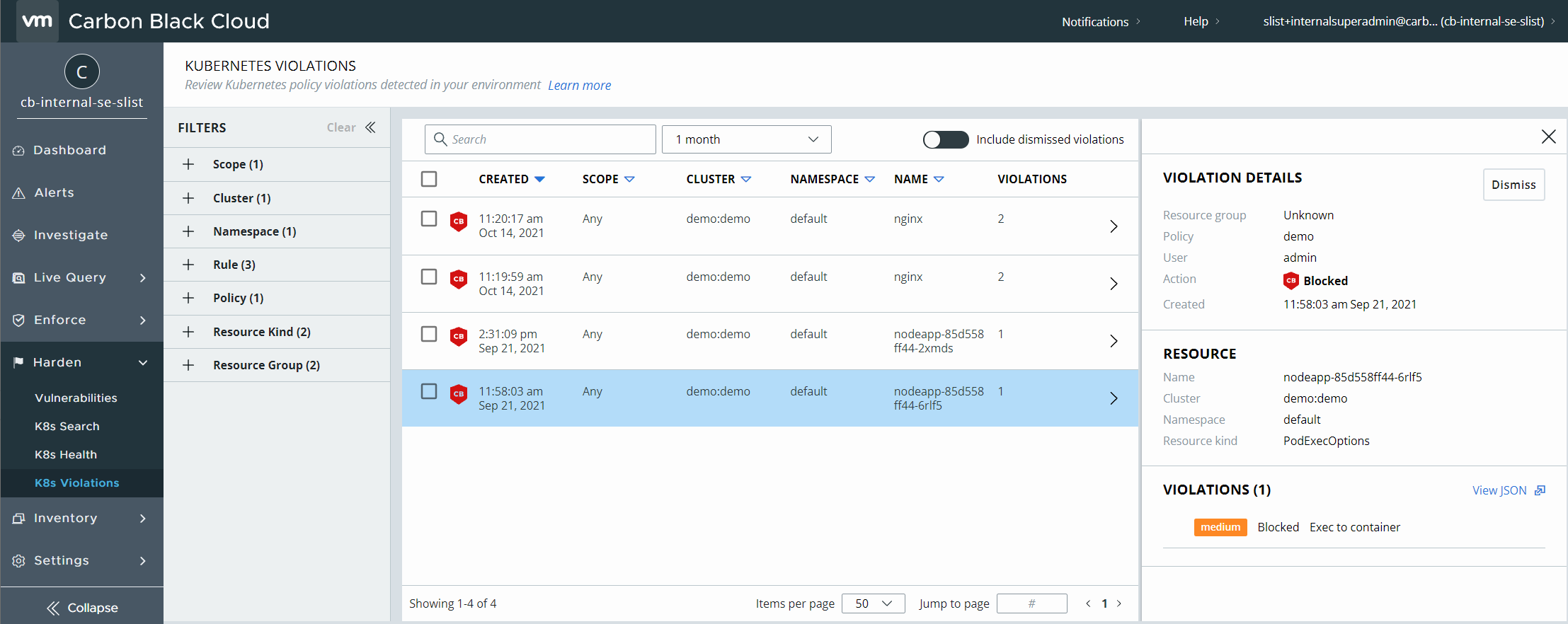
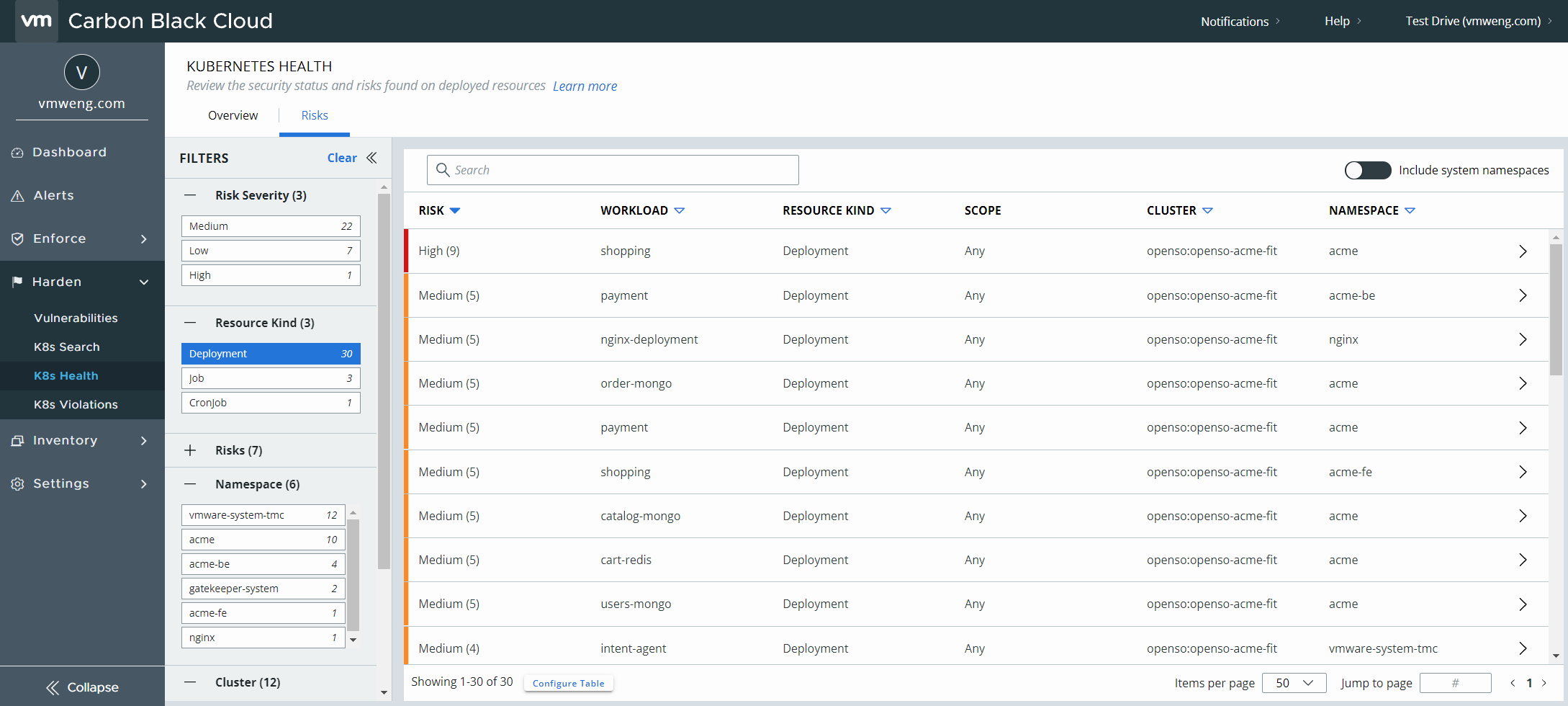
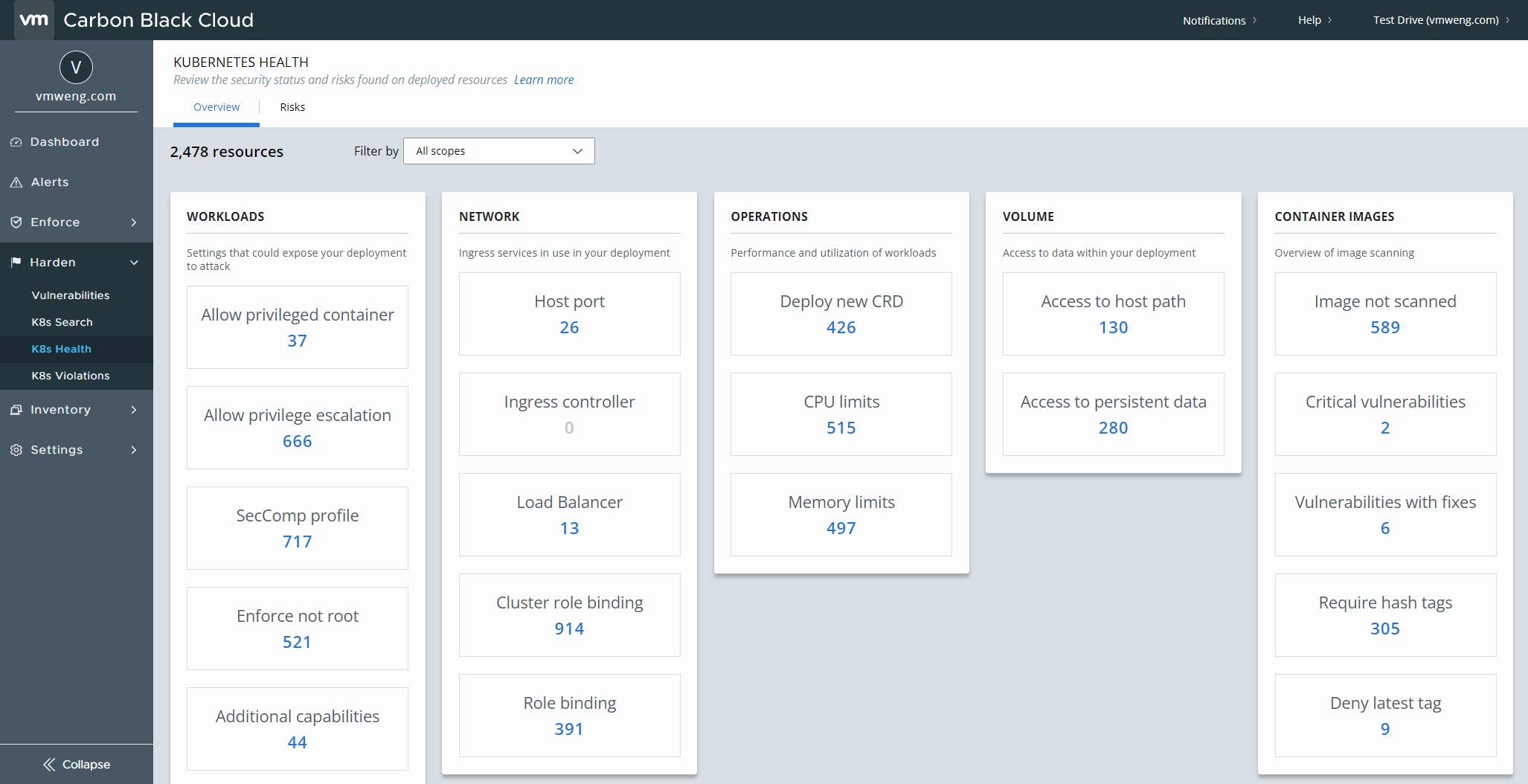
Complete visibility into Kubernetes security posture
VMware Carbon Black Cloud Container provides the visibility and control that DevOps and security teams need to secure Kubernetes clusters and the applications deployed on them. It delivers instant visibility into all workloads with the ability to enforce compliance, security and governance from a single dashboard. This single pane of glass gives complete visibility into the security posture across Kubernetes clusters and namespaces, including:
- Visibility into Kubernetes clusters and workload inventory
- A combined view of all vulnerabilities, misconfiguration, and rules violations.

- Workload configuration risk reporting and governance.

- A consolidated risk score aggregated for all workload attributes to prioritize remediation With VMware, application security and DevOps teams gain full visibility into Kubernetes environments to proactively harden workloads, and better identify and reduce the risks posed by vulnerabilities and misconfigurations.
Image Scanning
A key reason why enterprises are turning to Kubernetes is that cloud-native services and practices boost developer productivity. As you put containerized applications into production, you need a secure way to store, scan, and sign your container images. A container image registry without management and security puts your cloud-native environment at risk.
Container images present some security challenges. Images are usually built by layering other images, which could contain vulnerabilities, and those vulnerabilities can find their way into production systems. Defects and malware can also affect container images. When the provenance of a container is dubious or unknown these risks increase.
Container image registries with the following functionality can reduce these risks:
- Scan images for vulnerabilities found in the Common Vulnerabilities and Exploits (CVE) database.
- Sign images as known and trusted by using a notary.
- Set up secure, encrypted channels for connecting to the registry.
- Authenticate users and control access by using existing enterprise accounts managed in a standard directory service, such as Active Directory.
- Tightly control access to the registry using the principles of least privilege and separation of duties.
- Enact policies that let users consume only those images that meet your organization’s thresholds for vulnerabilities.
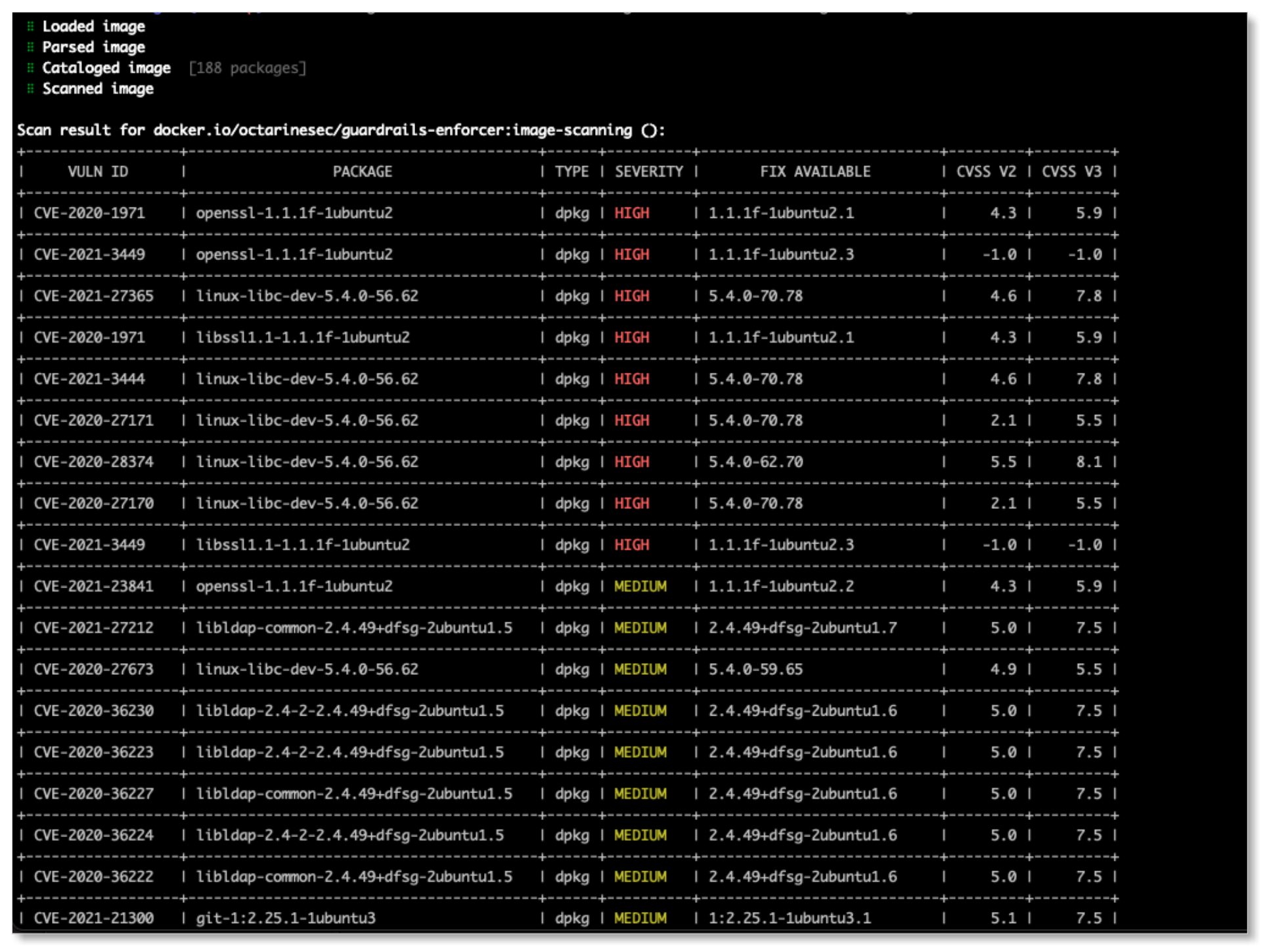
Vulnerability Scanning
Containers often use base images of operating systems like Ubuntu and CentOS from a public image repository, such as DockerHub. The packages of an operating system and the applications on it, however, can contain vulnerabilities.
Vulnerability scanning helps detect known vulnerabilities to reduce the risk of security breaches. Identifying a vulnerability on an image and keeping the vulnerability from going into production reduces the attack surface of a containerized application.
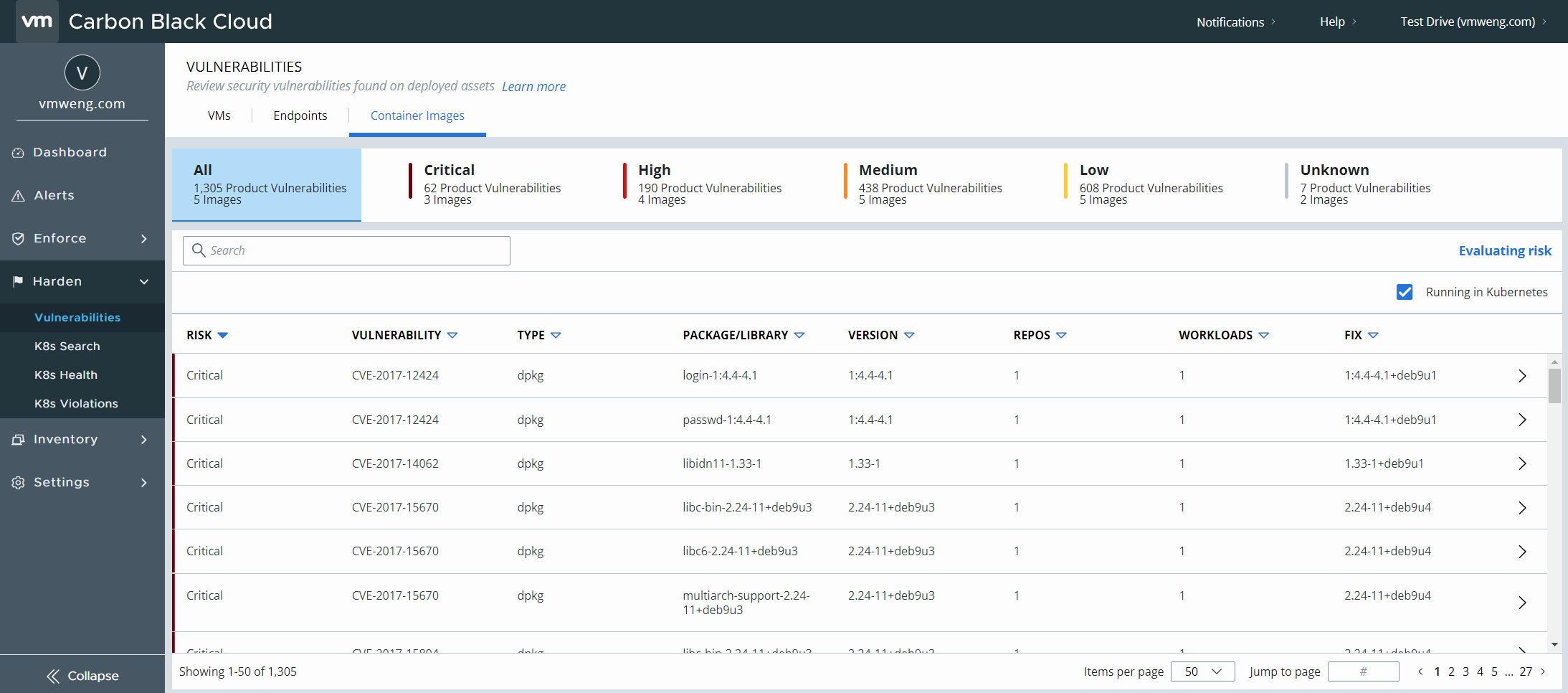
Image Scanning CLI
The cbctl command-line tool is inspired by Kubernetes kubectl and lets you control your Carbon Black Cloud Container and Kubernetes workload security. CLI is Used manually by developers or integrated with CI. It scans for the images and k8s objects for risk and vulnerabilities and validates against policy. For configuration, cbctl looks for a file named config in the $HOME/.cbctl directory. You can specify other cbctcl config files by setting the --config flag. For more information, see Image Scanning CLI.
Compliance & Policy Automation
When we talk about compliance in this context, we’re talking about both industry standards such as CIS Benchmarks and the customer’s own organizational requirements. Typically, the application security team will define the security policies they want in place for their organization, and the DevOps team will create the policies and ensure compliance.
Carbon Black Cloud Container solution’s compliance policy automation capabilities help customers by:
• Shifting left into the development cycle to detect and prevent vulnerabilities at build
• Creating automated policies to enforce secure configuration
• Ensuring compliance with organizational requirements and industry standards such as CIS benchmarking.
• Leveraging pre-built templates and customize policies.
Top 5 Things you should know about Containers
- What to keep in mind if you’re considering Containers?
-
Containers are just one of many important features of cloud-native development. If you’re moving to containers, there are multiple elements to bear in mind:
Understand containers and container orchestration
To get started with containers, you need to know about both containers and container orchestration.
Container orchestration helps manage the complexity of the container lifecycle. This becomes especially important when you’re operating distributed applications and large numbers of containers.
Kubernetes is an open-source container orchestrator. Kubernetes automates deployment, load balancing, resource allocation, and security enforcement for containers via declarative configuration and automation. It keeps containerized applications running in their desired state, ensuring they’re scalable and resilient.
You can access Kubernetes in a number of ways: as open-source, as a service in most public clouds, or via prepackaged Kubernetes distributions. There is an ecosystem of projects and products that supplements and extends the abilities of containers and Kubernetes.
See KubeAcademy to learn more about Kubernetes and container orchestration. Also, see Kubernetes vs. Docker learn how the two technologies relate to one another.
- Container lifecycle security - A Shift-Left Approach
-
As organizations adopt new ways of deploying containerized applications, they need to take a DevSecOps approach, changing the way they implement and manage security policies. Like testing, integration, and deployment, security needs to be built in at the ground level of application development and automated as much as possible.
Baking security into an application early in the container lifecycle is the so-called “shift left” of an organization’s security model. Security teams, working with development and operations teams, can adapt existing governance and compliance policies to accommodate the new container and application lifecycle and new tools. Development and delivery teams are then responsible for the implementation of those practices, performing the day-to-day decision-making around the security of applications, and providing evidence demonstrating that they are meeting the organization’s policies.
- Why is DevSecOps critical for containers and Kubernetes?
-
As organizations adopt new ways of deploying containerized applications, they need to take a DevSecOps approach, changing the way they implement and manage security policies. Containers facilitate DevSecOps practices by improving handoffs between development and operations teams. Also, DevSecOps is critical for Kubernetes as it improves developer productivity when successfully integrated.
- When should I use Kubernetes?
-
Knowing when to use Kubernetes is a matter of scale. Running containers manually may be OK for developers, but running complex, multi-container applications, ensuring availability, and scaling by adding multiple container instances quickly creates complexity that increases with the number of containers and host systems. Kubernetes was designed specifically to address the operational concerns of running containers in production. It recognizes the anticipated—and unanticipated—complexities of running containers on different systems and in different environments.
- Difference between a VM and a Container?
-
Containers vs. VMs
At the simplest level, the difference between a virtual machine (VM) and a container is that every VM runs a full or partial instance of an operating system, whereas multiple containers share a single operating system instance. A container is a lightweight, standalone, executable package that—in conjunction with the host system—includes everything necessary to run an application such as code, runtime, system tools, system libraries, and settings, enabling multiple containerized applications to run independently on a single host system. Since multiple containers can run inside a VM, you can combine the benefits of both.
Multiple containers can run in lightweight VMs to increase security and isolation. The VM creates an infrastructure-level boundary that container traffic cannot cross, reducing exposure if a service is compromised.

Summary and Additional Resources
Conclusion
This document provides you with a good understanding and overview of Carbon Black Container Cloud Security Solution Protection and its capabilities. To learn more about the product explore our hands-on lab and TestDrive experience.
Change Log
The following updates were made to this guide:
|
Date |
Description of Changes |
|
2019/10/17 |
|
Additional Resources
For more information about Endpoint Standard, explore the Mastering Container Security. The activity path provides step-by-step guidance to help you increase your understanding of the Carbon Black Endpoint Standard, including articles, videos, and labs.
You can also see the Carbon Black Container FAQ which answers the most common questions about Carbon Black Cloud Container.
Like to learn more about Container Runtime Security? See Announcing Container Runtime Security for VMware Carbon Black Container
Authors and Contributors
With significant contributions from:
- Stephane List, Staff Technical Marketing Architect, Carbon Black